Accessing an automobile’s computer systems or data without authorization may soon result in a six-figure fine in the US.
A draft bill (pdf) proposed Wednesday by the House Energy and Commerce Committee establishes a civil penalty of up to $100,000 to any person who accesses “without authorization, an electronic control unit or critical system of a motor vehicle, or other system containing driving data for such motor vehicle, either wirelessly or through a wired connection.” The penalty would be applicable multiple times for each system accessed.
It is unclear who would need to grant “authorization” or what “access” even constitutes, based on the text of the bill. An interpretation that determined that authorization could only be granted by the manufacturer would have wide-ranging implications for tinkerers, researchers, and mechanics alike. Presumably, this interpretation could mean that a car owner can’t access her own driving data without permission from the manufacturer. Another possibility is that a non-dealership mechanic would need clearance to use certain diagnostic equipment on a car.
It’s not far fetched; the auto industry is already trying to establish that car owners don’t actually own all of their cars, and therefore can’t do things like inspect the code running on their computers.
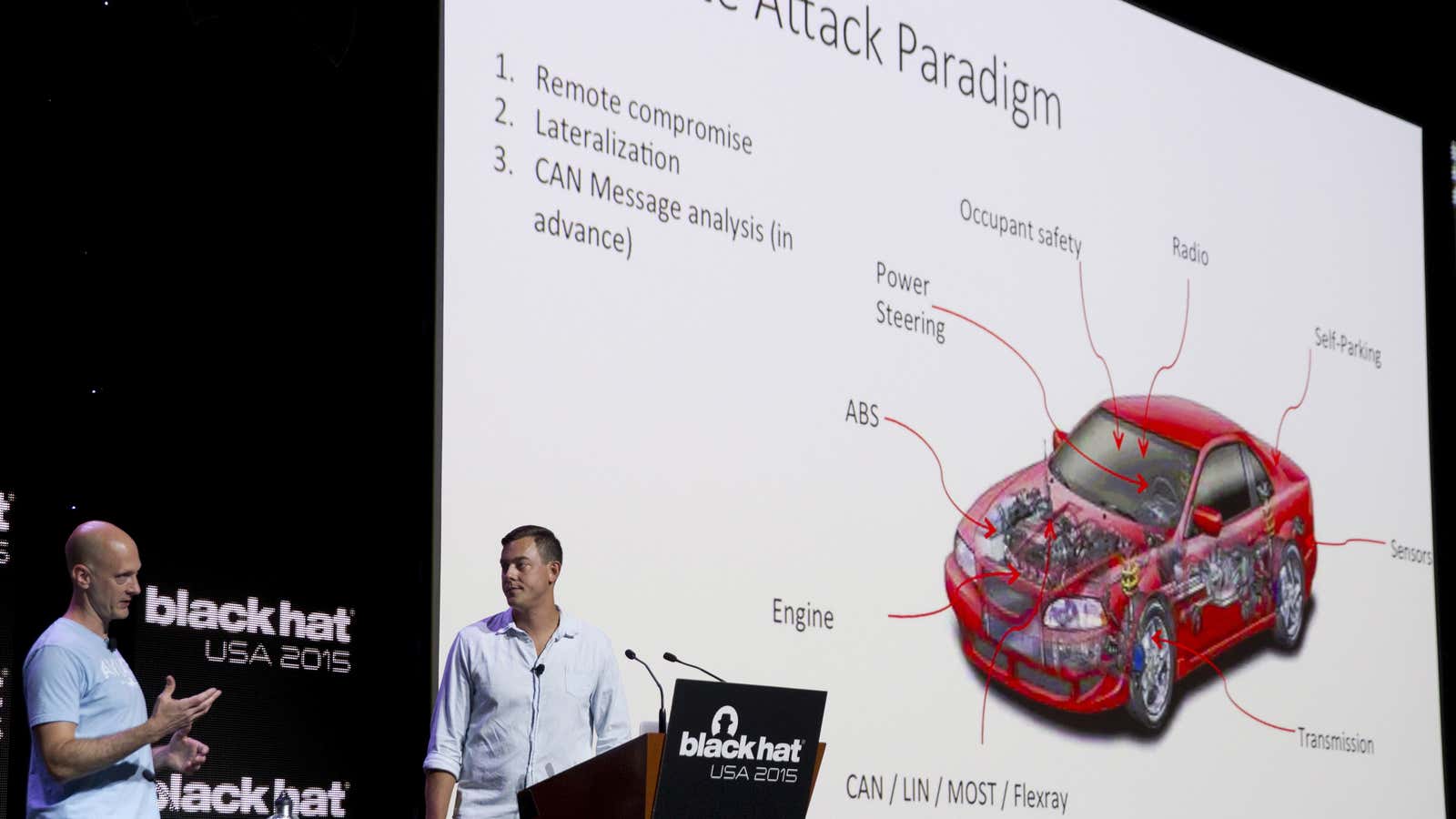
The bill comes after a series of high profile incidents where researchers have found security vulnerabilities in automotive computer systems, as well as reports of criminals exploiting flaws. That’s all on top of every-day enthusiasts who—in a long American tradition—tinker with and modify their cars.
In July, two researchers revealed they were able to hijack a Jeep Cherokee wirelessly. They were able to perform juvenile tasks like blast Kanye West music from the radio. They also were able to disable the brakes and accelerator of the car. Chrysler, Jeep’s corporate parent, issued a recall for the vehicles days later to patch the vehicles’ software.
In August, another researcher was able to unlock and start OnStar equipped vehicles from GM.
Thieves reportedly have been able to break into cars by spoofing the signal of keyless entry fobs.
Not all security vulnerabilities require active efforts. Cars have also been found to leak information all by themselves. Tire pressure monitors have been found to broadcast their readings on radio frequencies that can be found and decoded.
The bill also calls for the creation of national standards and guidelines on securing the technology and data in automobiles.