This article was updated at 5pm EST on Feb. 6.
A cyber-attack on health insurance giant Anthem, which potentially compromised the personal information of tens of millions of customers, is linked to state-sponsored Chinese hackers, intelligence officials and others brief on the investigation told Bloomberg and the Washington Post.
That’s particularly worrisome for the US government, given Anthem’s customer list, which includes, among others, Michael Daniel, US president Barack Obama’s chief adviser on cyber-security. (He plans to reset his password.)
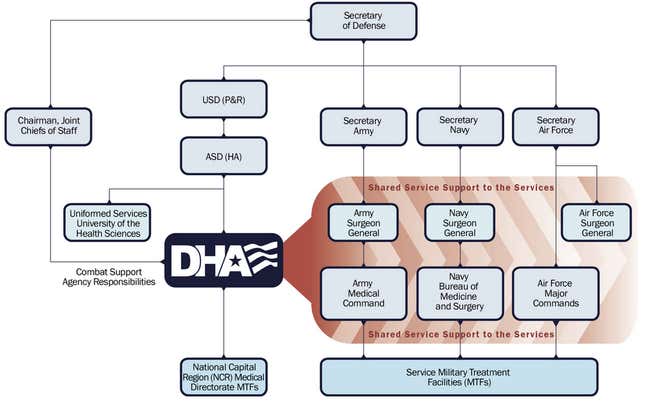
But Daniel is only one of thousands of US government employees who could have been potentially affected by the hack, many of them currently or formerly tasked with US security and defense. That’s because one Anthem division, National Government Services, specializes in managing federal health care claims, and includes among its top clients the Defense Health Agency (DHA), which manages health care for the US Department of Defense, as well as the US Department of Veteran Administration, which covers retired military.
Update: An Anthem spokesperson told Quartz that “National Government Services’ investigation indicates that National Government Services was not impacted by the Anthem cyber-attack. Medicare information managed directly by National Government Services is maintained on systems protected by the Department of Health and Human Services and the Centers for Medicare and Medicaid Services. These are not the systems which were compromised in the external cyber-attack on Anthem.”
The Defense Health Agency serves everyone from the Secretary of Defense on down to active armed forces personnel:
Anthem clients also include defense contractors Northrup Grumman and Boeing.
Some elements of the Anthem hack have been traced back to China’s infamous People’s Liberation Army’s Unit 61398, which has been implicated in many of the recent cyber-attacks against the US government and private companies in the past, two unnamed intelligence officials told Bloomberg. China-based hackers have targeted US defense contractors and former government employees in attacks in recent years in a campaign cyber-security company CrowdStrike has dubbed “Deep Panda.”
Anthem said that hackers have accessed “names, birthdays, medical IDs/social security numbers, street addresses, email addresses and employment information, including income data.” Security experts believe the information from the Anthem attack and other recent large-scale hacks could be used to create well-rounded profiles of potential espionage targets—part of a relatively new kind of dual-pronged hacking attack that is also plaguing financial institutions.
Bank security experts and government officials are seeing an uptick in these dual-pronged attacks, as the American Banker explained recently:
Hackers cross-reference data obtained from different sources — card numbers from Home Depot, for example, and Social Security numbers from another breached organization. Then they call the bank and ask to change the PIN on the card account, which some banks will do for a customer who can provide a Social Security number and card number. (Some even offer automated systems to take care of this.) Hackers can stitch all this data together and sell it on the black market as a fully emulated debit card that allows an individual to walk up to an ATM, enter the PIN and withdraw cash.
The same basic method used by hackers interested in financial gain could also be used by a hostile intelligence agency to compile dossiers of personal information on potential targets with the government or a defense contractor. “If you have a rich database of proclivities, health concerns and other personal information, it looks, from a Chinese intelligence perspective, as a way to augment human collection,” a CrowdStrike executive told Bloomberg.
National Government Services’ website said that it has “some of the most secure and reliable information technology infrastructure in the industry.” Parent company Anthem did not encrypt customers’ data, one of the most basic ways to protect it from being used by hackers.
Update: The Anthem spokesperson said that Anthem “encrypts data in motion–data that moves between servers.” But the company does not encrypt “data at rest,” or stored in its databases. “Anthem did everything it could to protect and monitor for this type of attack,” she said. “Due to the nature of this sophisticated attack, the actions taken against the system appeared to be normal workflow. There is no indication that this type of attack could have been prevented or caught prior to exposing data.”
