
This building on the outskirts of Shanghai is the home of Unit 61398 of the Chinese military, which is responsible for the preponderance of digital espionage against American companies and the US government, according to a report just released by the computer security firm Mandiant.
The specificity of the report—and its treatment in a lengthy front-page article in the New York Times—is likely to inflame discussion of the threat posed to multinational corporations by state-sponsored hackers in China. Mandiant said Unit 61398, sometimes known in the US as “Comment Crew,” was responsible for attacks on at least 141 companies. Previous reports have identified Coca-Cola, Halliburton, and the European Union as among the victims of Comment Crew.
Here is another image from the Mandiant report identifying the location of Unit 61398 on Datong Road in Shanghai:

Mandiant said the building was built in 2007 and contains 130,663 square feet over 12 floors. “China Telecom provided special fiber optic communications infrastructure for the unit in the name of national defense,” the report notes.
The hackers of Unit 61398 use elaborate ruses to infiltrate computers that sit behind corporate and government networks, then maintain access for an average of 356 days, downloading files ranging from emails to contracts. Mandiant released a video of what it said it was an actual hacker in Unit 61398, nicknamed “DOTA,” engaging in cyber espionage:
The Chinese government denies any involvement in computer hacking and says any such activity emanating from China is the work of rogue hackers not sponsored by the state. But plenty of reports, including this latest one, have suggested otherwise. Here’s a map of victims of hacking by Unit 61398, which Mandiant refers to as Advanced Persistent Threat (APT) 1:
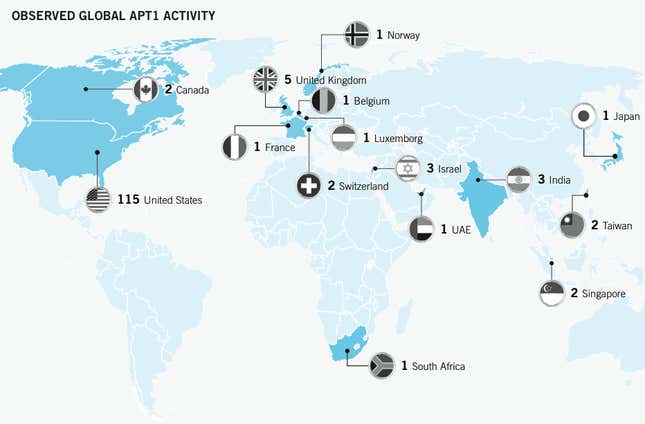
The Mandiant report doesn’t identify any victims by name, though others have in the past, but says the hacking of companies has spanned 20 major industries. (The Times reports that Unit 61398 wasn’t responsible for recent hacking of the newspaper’s servers.) This timeline gives a sense of where the hackers have seemed to focus their interest at various times:
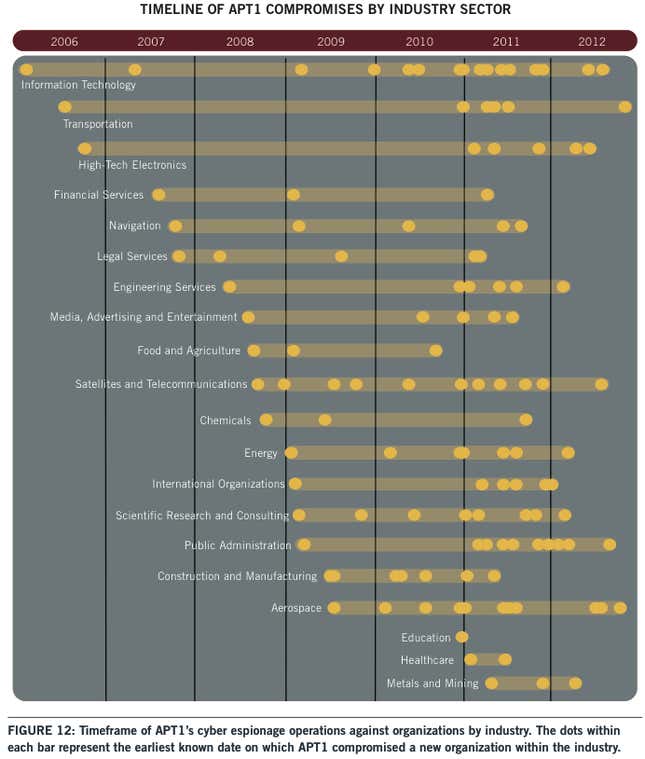
The report, which is available as PDF here, also details the techniques and infrastructure of Unit 61398 in an attempt to aid defenses against the attacks—and, of course, to market Mandiant’s services for the same.