The Petya ransomware attack made $20k less than WannaCry in its first 24 hours
An ongoing ransomware attack that knocked out critical services in Ukraine on Tuesday, then proliferated throughout Europe and the United States, has shown no signs of stopping. Similar to the WannaCry attack last month, the new malware locks users out of their files and demands they pay $300 in bitcoin to get them back.
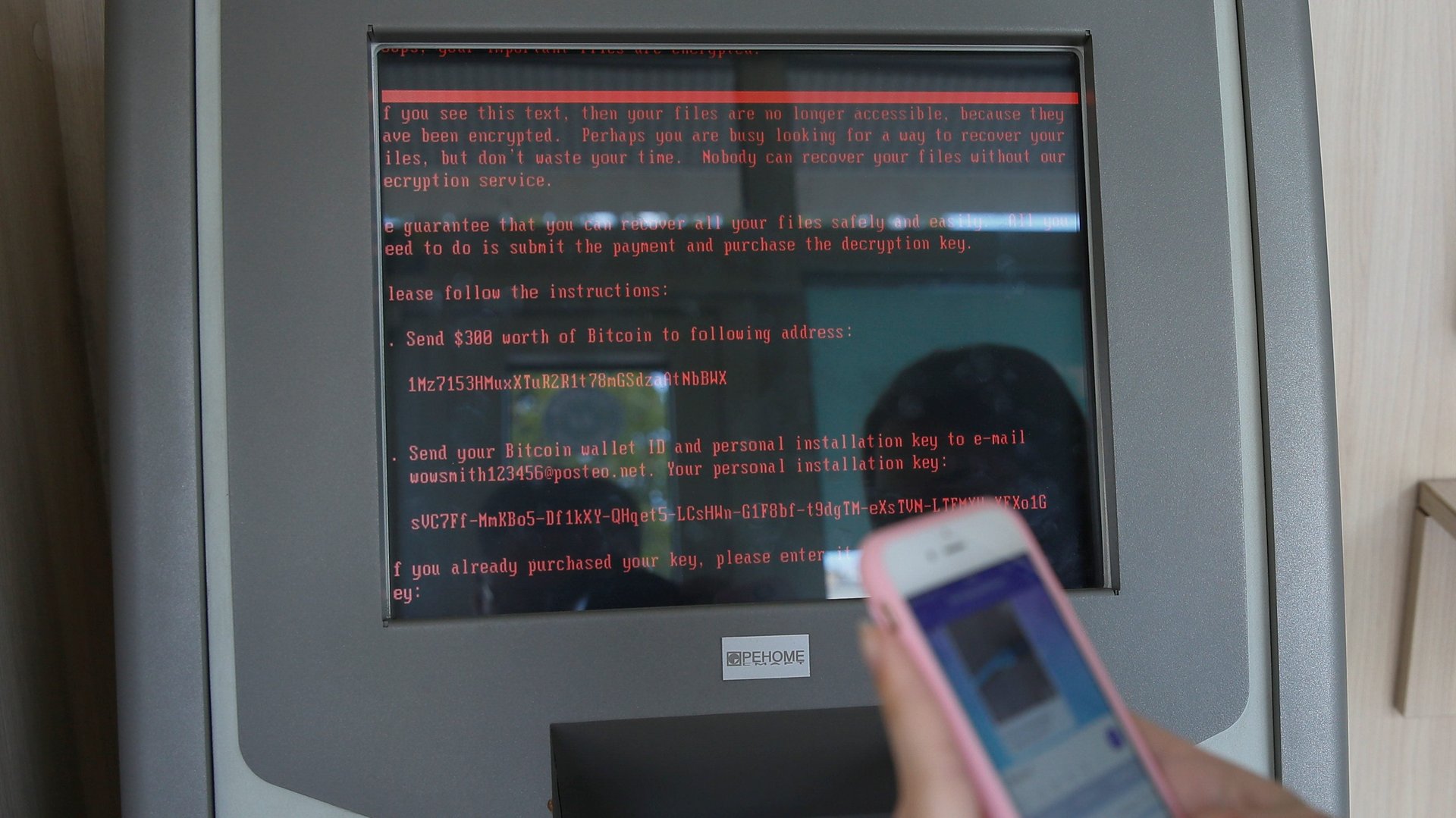

An ongoing ransomware attack that knocked out critical services in Ukraine on Tuesday, then proliferated throughout Europe and the United States, has shown no signs of stopping. Similar to the WannaCry attack last month, the new malware locks users out of their files and demands they pay $300 in bitcoin to get them back.
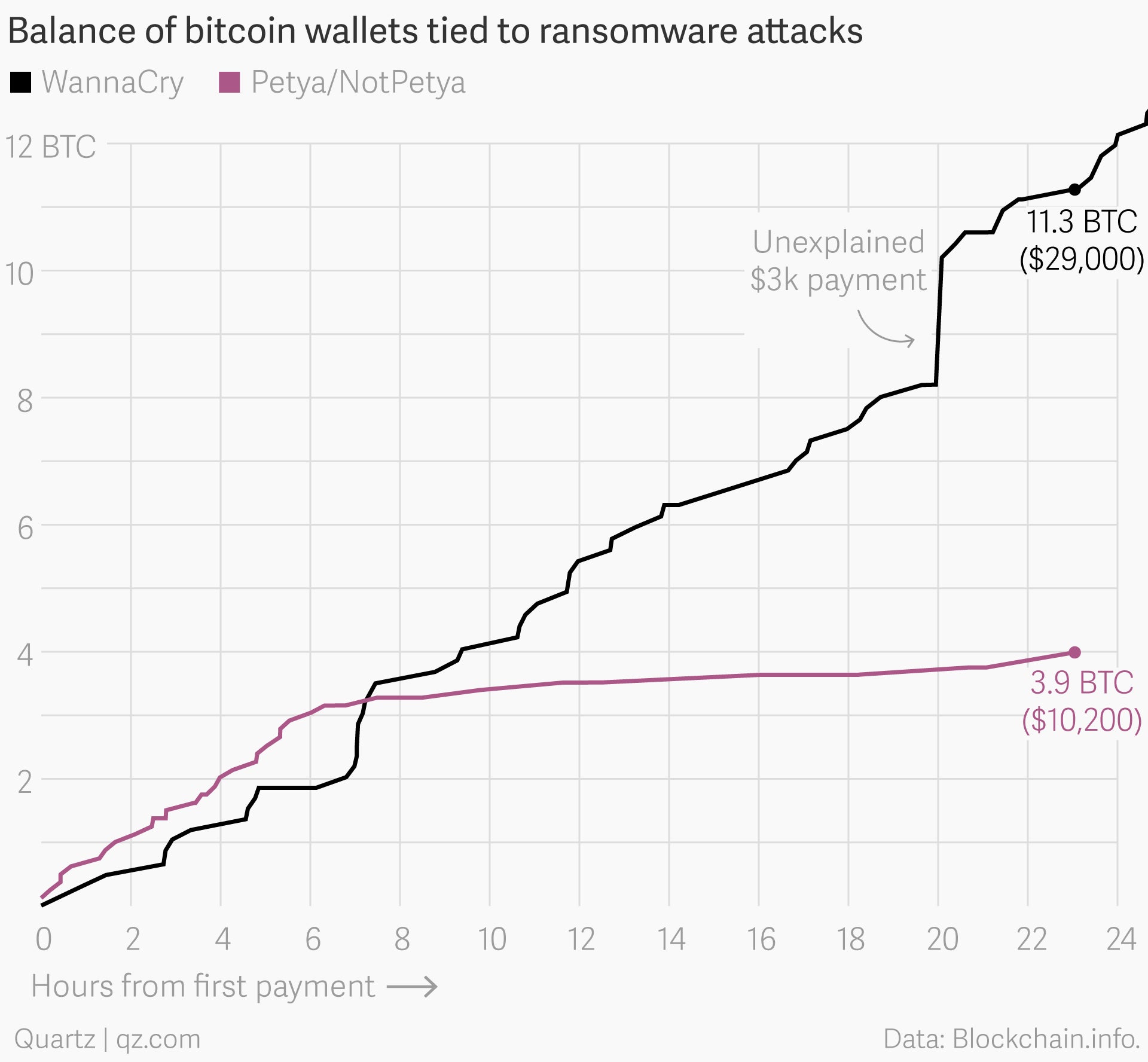
Known as either Petya or NotPetya, depending on who you ask, the ransomware has now been spreading for more than 24 hours. And although it’s already hit many companies, including the British advertising agency WPP, the Danish shipping and oil group Maersk, and the pharmaceutical giant Merck in the United States, Petya has so far made roughly $20,000 less than the WannaCry attack did on May 12, going by the current value of bitcoin.
Petya and WannaCry were both built with hacking tools that were allegedly developed by the US National Security Agency (NSA) and leaked to the public in April by a hacker group calling itself the Shadow Brokers. Experts have said that the success of WannaCry, which infected nearly 300,000 computers worldwide including hospitals in the British health service, was largely due to the power of the leaked tools.
Just like in the WannaCry attack, computers infected with Petya display a message with instructions for the user.
“If you see this text, then your files are no longer accessible, because they have been encrypted,” the message says. “Perhaps you are busy looking for a way to recover your files, but don’t waste your time. Nobody can recover your files without our decryption service.”
In order to get their files decrypted, the message says, users must send $300 to a particular bitcoin address, a long string of letters and numbers displayed below the message:
1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX
WannaCry worked in very much the same way, also demanding $300 in bitcoin for file decryption.
All bitcoin transactions, though anonymous, are publicly recorded on the blockchain. Because Petya and WannaCry both used bitcoin, every ransom payment made to the hackers behind both attacks can be viewed by anyone.
We pulled all of the transactions from both attacks from Blockchain.info to create the charts above and below. We’ve also created Twitter bots that tweet each time a ransom is paid to the hackers behind both attacks: @actual_ransom tweets WannaCry payments; @petya_payments tweets, well, Petya payments.
In the six weeks since the WannaCry attack, payments have continued to trickle in to its three associated bitcoin addresses, which have now amassed nearly 52 bitcoins, or roughly $130,000 USD, depending on the volatile exchange rate of bitcoin. Many consider that to be a paltry sum for an attack that locked doctors in the UK out of patient records and forced emergency rooms to send patients to other hospitals.
Here’s what the trajectory of the WannaCry wallets looked like in the ransomware’s first five days:
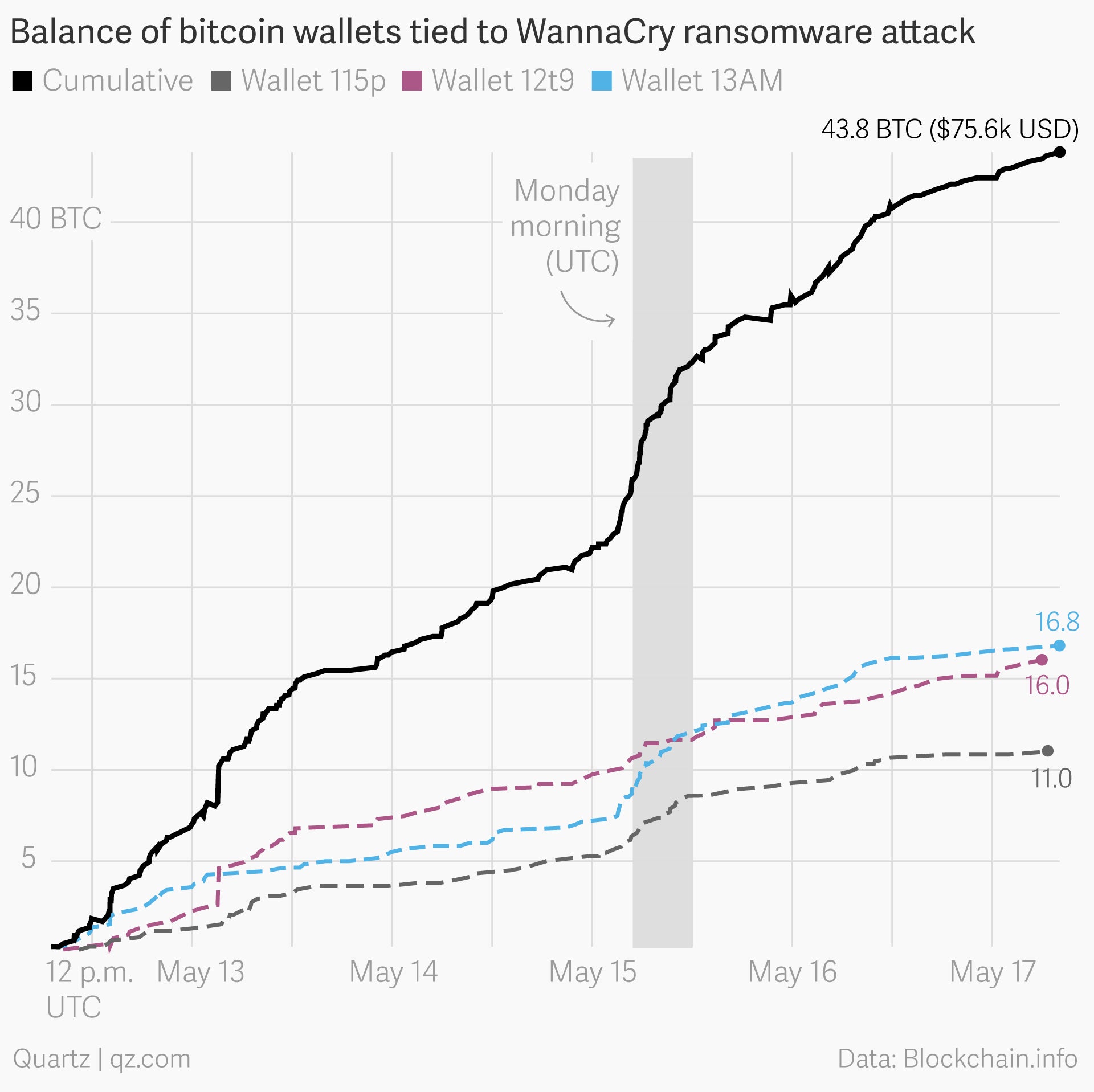
That upward trend has now flattened out, with just a couple of new payments each week, and the hackers behind the attack have not yet attempted to move the money. Because they used just three easy-to-track accounts for the attack, as opposed to generating a unique one for each infected computer, they would likely not be able to get their hands on the money without being caught by law enforcement.
Whether the attackers behind WannaCry were ever interested in the money, however, remains an open question. And the same question has already been raised about the hackers behind Petya.