Researchers say figuring out who you are based on your browsing data is “trivial”
In April, US president Donald Trump signed a resolution that allows internet service providers (ISPs) to collect private browsing history from American internet users—without their permission—and sell it to third parties. Advocates of the measure, which repealed pending regulations put in place by the Obama administration, said the rules would have put the ISPs at a disadvantage in competing with Google, and that it was no big deal because the data was anonymized anyway.

In April, US president Donald Trump signed a resolution that allows internet service providers (ISPs) to collect private browsing history from American internet users—without their permission—and sell it to third parties. Advocates of the measure, which repealed pending regulations put in place by the Obama administration, said the rules would have put the ISPs at a disadvantage in competing with Google, and that it was no big deal because the data was anonymized anyway.
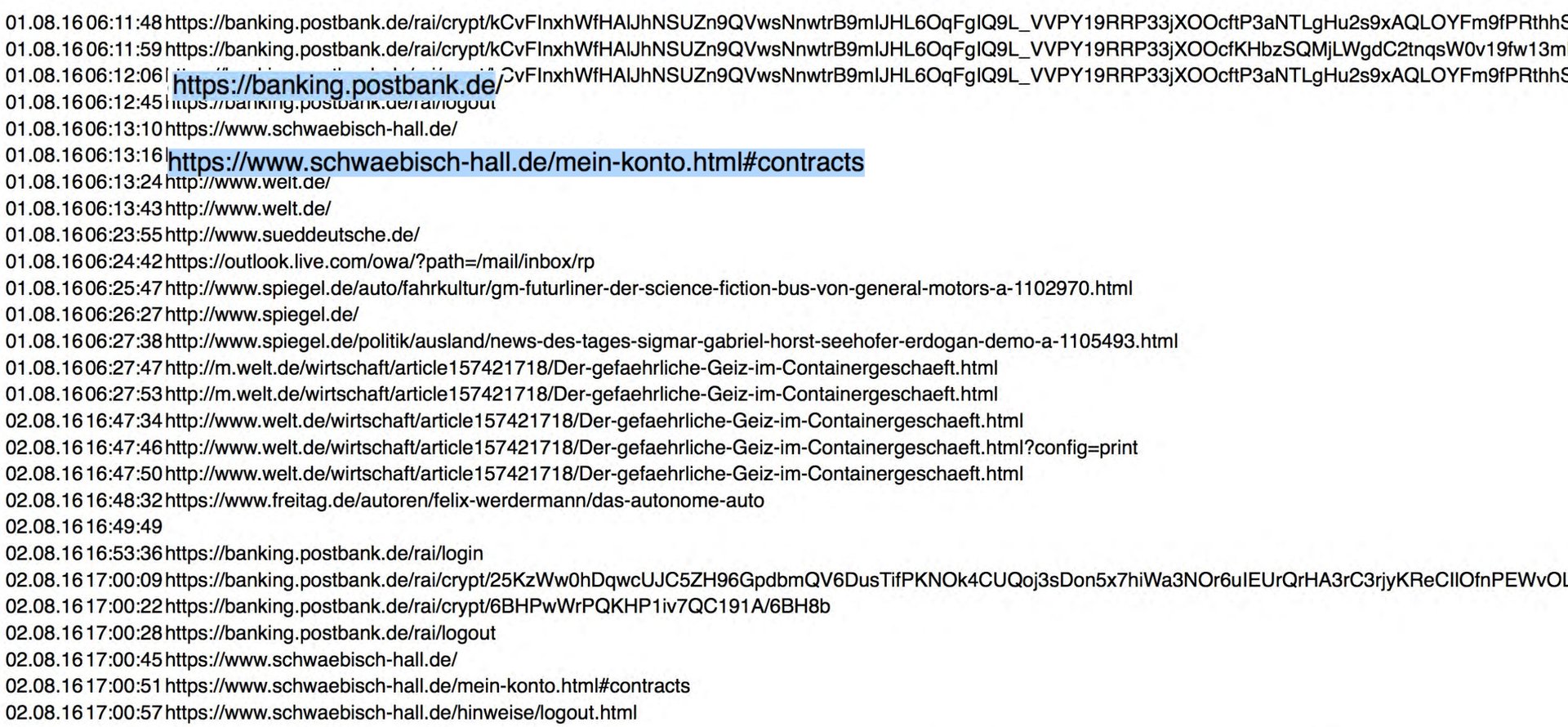
However, findings presented at a hacking conference in Las Vegas on July 28 suggest otherwise. Security experts Svea Eckert and Andreas Dewes analyzed anonymized browsing data collected from 10 Chrome extensions that tracked German users’ web activity, and successfully matched the data to many of the people it was mined from. Their analysis uncovered, for example, the porn-browsing activity of a judge and the drug habits of a German politician.
In total, the researchers linked 3 million German citizens to their browsing data, and said doing so was “trivial.” In many cases all it took was identifying page visits to login pages where the URL indicates what user is logging in. In others, the researchers simply had to match a visited URL at a given time with that URL being publicly shared on social media at the same time.
“With only a few domains you can quickly drill down into the data to just a few users,” Dewes said.
Those same methods of identification, of course, could likely be used to de-anonymize any browsing data that includes URLs and the times they were visited.
The data the researchers analyzed came from “clickstreams,” which were built into Chrome extensions to specifically track minute-by-minute browsing activity to target advertisements. The good news is that, while ISPs in the US inherently have the ability to collect the same kind of browsing data directly from their customers, the country’s largest ISPs have said they will not sell the data to third parties, despite the lack of regulation against the practice.