The hackers who broke into Equifax exploited a flaw in open-source server software
Correction (Sep. 8, 7:20 p.m.): An earlier version of this article said the vulnerability exploited by the hackers who broke into Equifax was the one disclosed on Sep. 4. It’s possible that the vulnerability that was targeted was one disclosed in March. We will update this post when we’ve confirmed which vulnerability it was.

Correction (Sep. 8, 7:20 p.m.): An earlier version of this article said the vulnerability exploited by the hackers who broke into Equifax was the one disclosed on Sep. 4. It’s possible that the vulnerability that was targeted was one disclosed in March. We will update this post when we’ve confirmed which vulnerability it was.
Update (Sep. 14, 12:15 a.m.): Equifax has confirmed the vulnerability that was targeted was the one disclosed in March; this article has been updated.
The credit reporting agency Equifax announced on Sept. 7 that hackers stole records containing personal information on up to 143 million American consumers. The hackers behind the attack, the company said, “exploited a U.S. website application vulnerability to gain access to certain files.”
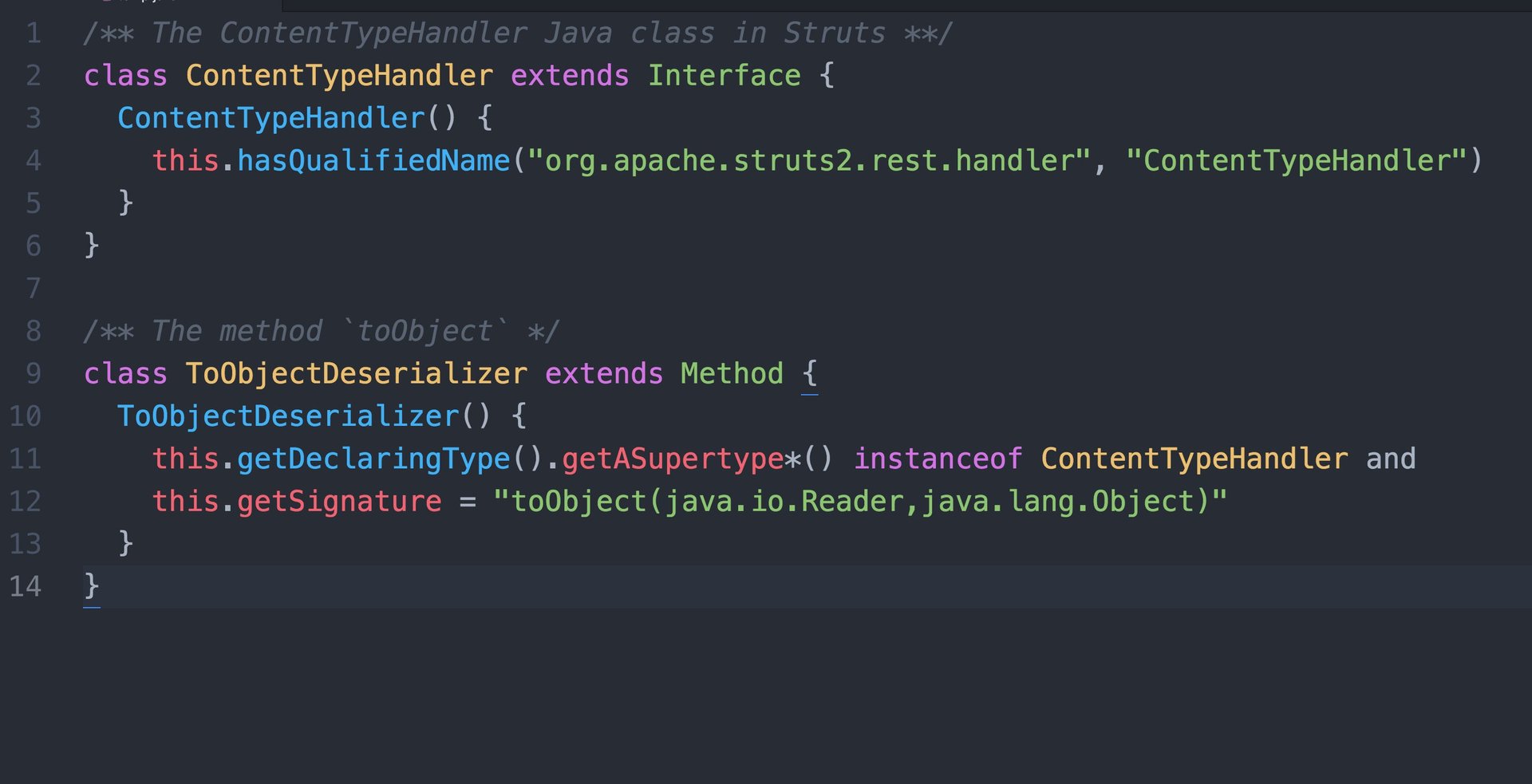
That vulnerability, according to a statement Equifax published on Sep. 13, was in a popular open-source software package called Apache Struts, which is a programming framework for building web applications in Java. A patch for the vulnerability was released on March 7, the same day it was announced. Equifax says hackers exploited the bug to break into its server two months later, in mid-May.
Apache Struts has been widely used by companies and government agencies for years. It’s currently in use by at least 65% of Fortune 100 companies, according to researchers who discovered a separate vulnerability in the software in early September.
“Organizations like Lockheed Martin, the IRS, Citigroup, Vodafone, Virgin Atlantic, Reader’s Digest, Office Depot, and SHOWTIME are known to have developed applications using the framework,” the researchers wrote in a blog post. “This illustrates how widespread the risk is.”
The vulnerability hackers exploited to break into Equifax relates to how Struts handles data sent to the server. Attackers can use file uploads to trigger a bug that allows them to send malicious code or commands to the server. After the vulnerability was disclosed on March 7, security researchers detected attacks that targeted it almost immediately.
A report on the data breach released by William Baird & Co. on Sep. 7 was the first indication that the Equifax hackers had targeted a vulnerability in Apache Struts, but it was unclear at the time which specific vulnerability it was.
Equifax said in its Sept. 7 statement that most of the consumer information accessed includes “names, Social Security numbers, birth dates, addresses, and in some instances, driver’s license numbers” as well as “credit card numbers for approximately 209,000 consumers.” The company added that 182,000 credit-dispute documents, which contain personal information, were also stolen.