What you need to know about the newly-discovered wifi bug that lets hackers snoop on your devices
In a short YouTube video posted Monday (Oct. 16), security researcher Mathy Vanhoef demonstrated how a hacker could intercept data transmitted from a wireless device—in this case an Android phone—by exploiting a new flaw he discovered in wifi authentication. The hack takes Vanhoef about four minutes to execute.
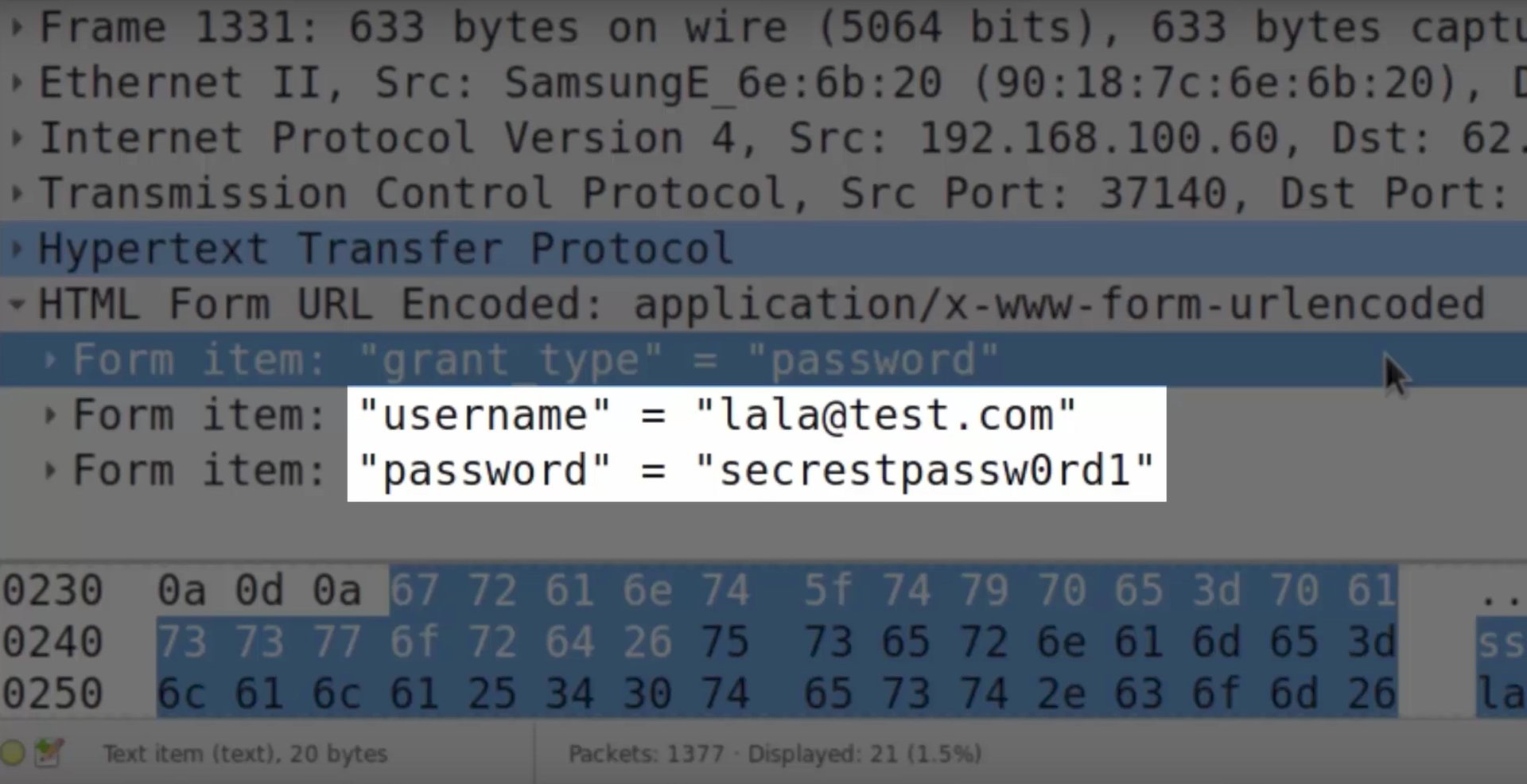

In a short YouTube video posted Monday (Oct. 16), security researcher Mathy Vanhoef demonstrated how a hacker could intercept data transmitted from a wireless device—in this case an Android phone—by exploiting a new flaw he discovered in wifi authentication. The hack takes Vanhoef about four minutes to execute.
Vanhoef calls the hack KRACK, short for “key reinstallation attack,” and explained in a blog post that it can be used to read data transmitted between a device and the wireless network it’s connected to, even if that network is password-protected and encrypted. KRACK exploits a vulnerability in Wi-Fi Protected Access 2 (WPA2), the encryption protocol most consumers and many organizations use to protect their networks.
The technique “can be abused to steal sensitive information such as credit card numbers, passwords, chat messages, emails, photos, and so on,” he wrote. “The attack works against all modern protected Wi-Fi networks. Depending on the network configuration, it is also possible to inject and manipulate data. For example, an attacker might be able to inject ransomware or other malware into websites.”
What you need to know
- When major vulnerabilities like this one are announced, the first thing you should do is update your devices. That includes computers, mobile phones, tablets, and routers. To be safe, update your devices immediately and then keep updating them over the next few weeks as companies release new patches.
- Android and Linux devices are the most susceptible to KRACK, according to Vanhoef.
- Google is planning to release a patch for Android phones “in coming weeks,” according to The Verge, starting with Pixel phones on Nov. 6. An ongoing problem with Android phones, which exacerbates this issue, is that a large portion of Android users neglect to update their devices regularly.
- Patches for Linux systems are available now for Debian users, and OpenBSD was reportedly patched over the summer.
- Security expert Kevin Beaumont said in a blog post that KRACK “realistically doesn’t work against Windows or iOS devices.” Still, Microsoft has already released patches for its supported Windows operating systems, and Apple told CNET it will be releasing software updates within a few weeks.
- This news does not necessarily mean hackers are actively exploiting the WPA2 vulnerability. Researchers like Vanhoef proactively search for and disclose flaws like this one for academic purposes, and to try to stay ahead of hackers. Announcing the existence of such vulnerabilities puts pressure on companies to develop patches for them, but can also prompt hackers to find ways to exploit them.
- While it’s impossible to know whether any hacker in the history of hacking independently discovered this vulnerability before Vanhoef’s announcement, it doesn’t appear likely. “There is currently no publicly available code out there to attack this in the real world — you would need an incredibly high skill set” to duplicate Vanhoef’s work, according to Beaumont.
- Hackers would have to be within range of a given wifi network to execute a KRACK attack.
- The technique KRACK employs highlights the importance of HTTPS, the secure protocol that websites can use to encrypt data transmitted between them and your web browser. The attack is particularly effective at extracting data your device transmits to websites that don’t use HTTPS or, as the video demonstrates, websites that use the protocol but have configured it incorrectly. As a general rule, always keep an eye on the address bar in your web browser, and look for the padlock icon, the word “Secure,” and the “https” at the beginning of the address you’re visiting.
This article was updated on Oct. 17 with new information on patch availability.