White House web security has lapsed because of the government shutdown
The security certificates authenticating more than 130 US government websites, including a subdomain at whitehouse.gov, have expired during the federal shutdown because the workers tasked with renewing them have been furloughed.


The security certificates authenticating more than 130 US government websites, including a subdomain at whitehouse.gov, have expired during the federal shutdown because the workers tasked with renewing them have been furloughed.
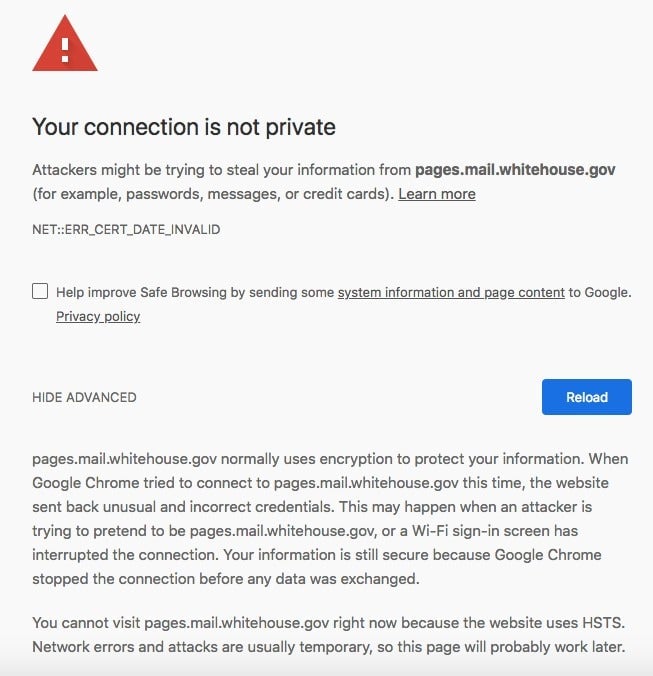
According to Netcraft, the UK-based internet security firm that released the list yesterday (Jan. 16), the number of government sites rendered “either insecure or inaccessible” was up from 80 one week earlier, an increase of 63%. Anyone who navigates over to “pages.mail.whitehouse.gov” will be greeted by the following warning:
pages.mail.whitehouse.gov normally uses encryption to protect your information. When Google Chrome tried to connect to pages.mail.whitehouse.gov this time, the website sent back unusual and incorrect credentials. This may happen when an attacker is trying to pretend to be pages.mail.whitehouse.gov, or a Wi-Fi sign-in screen has interrupted the connection. Your information is still secure because Google Chrome stopped the connection before any data was exchanged.
With the government partially unfunded due to the ongoing stalemate between Democrats and Donald Trump over his insistence on spending $5.7 billion for the border wall he has promised supporters, about 800,000 employees across dozens of agencies have been off the job since Dec. 22. Since the furloughed workers are prohibited by law from working—or even accessing their work emails—during the shutdown, the digital safety protocols, known as TLS (Transport Layer Security) certificates, will have to wait to be renewed.
In addition to parts of the official White House website, for which the security certificate expired Jan. 15, the affected sites have impacted the Federal Aviation Adminsitration (FAA), the Justice Department, and the Federal Financial Institutions Examination Council Anti-Money Laundering InfoBase. Each certificate runs about $399 per year.
The TLS certificate for https://manufacturing.gov expired Jan. 14. When a user tries to access the page, a browser warning appears:
This server could not prove that it is manufacturing.gov; its security certificate expired 4 days ago. This may be caused by a misconfiguration or an attacker intercepting your connection.

An internal Justice Department webpage, at https://ows2.usdoj.gov, is altogether unreachable. Its security certificate, under the aegis of GoDaddy, expired Dec. 17, 2018 and was never renewed. The certificate for https://www.disasterhousing.gov expired Dec. 28.
Paul Mutton, the Netcraft consultant who discovered the expired security protocols, told the Washington Post that the actual number of affected sites could be far higher, as some TLS certificates cover multiple pages for the same agency.
The Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) has furloughed 43% of its staff, per Axios. The National Institute of Standards and Technology, which manages America’s cybersecurity framework, has just 49 of its 3,000 employees on duty.
The government sites have not in fact been compromised, but to many people it certainly will appear that way, Chris Vickery of cybersecurity firm UpGuard, told the Post. “It’s likely to be a very big, misunderstood situation. My grandmother, she communicates with friends and gets recipes online. If she went to a government website and saw a warning saying ‘This certificate is no good, it could be a bad guy’— she would freeze up.”