The US military spent $33 million on tech known to be vulnerable to Chinese cyberespionage
The US Department of Defense (DoD) purchased and used millions of dollars worth of electronics last year containing “known cybersecurity vulnerabilities” that make them particularly susceptible to Chinese government espionage. The findings are included in a recent audit (pdf) by the Pentagon’s Inspector General (IG) for DoD cyberspace operations, which warns that “missions critical to national security could be compromised” if the military does not take swift action.


The US Department of Defense (DoD) purchased and used millions of dollars worth of electronics last year containing “known cybersecurity vulnerabilities” that make them particularly susceptible to Chinese government espionage. The findings are included in a recent audit (pdf) by the Pentagon’s Inspector General (IG) for DoD cyberspace operations, which warns that “missions critical to national security could be compromised” if the military does not take swift action.
Some models or brands of so-called COTS (commercial off-the-shelf) technology can allow adversaries access to communications infrastructure, command and control systems, and intelligence, surveillance, and reconnaissance networks, says the partially redacted IG report.
To that end, at least $32.8 million in COTS purchases made by the US Army and Air Force during the 2018 fiscal year were singled out for concern. The products include software, cameras, and networking equipment red-flagged by the Department of Homeland Security (DHS) and the Joint Chiefs of Staff Intelligence Directorate, as well as computers that have been banned for use by State Department employees since 2006.
Repelling cyberattacks has become an increasingly worrisome problem for the military since the DoD was hit with its first significant cyberattack from China in 2003. Last year, the Chinese government hacked into a US Navy contractor’s computer network, gaining access to highly sensitive secrets about a classified undersea missile program. Also last year, a breach of DoD travel records exposed the personal information and credit card data of tens of thousands of servicemembers and civilians, although that has not been explicitly linked to Beijing, which reportedly maintains a cyberespionage force with nearly 200,000 members (pdf) spanning both the military and private sectors. What’s more, a report issued last October by the Government Accountability Office found “mission-critical cyber vulnerabilities in nearly all weapon systems” developed by the US military between 2012 and 2017.
“The Chinese have already broken into my stuff,” Army acquisitions official Lt. Gen. Paul Ostrowski told attendees at an event earlier this month. “The personnel system has been broken into. This is something that has risen to the top of the concern list. Not only within the Army, but within [the Office of the Secretary of Defense].”
Unheeded warnings
As much as 80% of the DoD’s systems are off-the-shelf items, or contain components that are commercially available, says the new IG report. Yet, there is no “approved products list to prevent unsecure items from being purchased.”
In one example highlighted by the IG, the Pentagon continued to buy and use video surveillance systems manufactured by two Chinese companies, Hangzhou Hikvision Digital Technology and Dahua Technology, for at least 16 months after the state department warned against it due to cyberespionage concerns. The DoD didn’t stop until August 2018, when Congress officially banned the federal government from doing business with the two firms.
The current items singled out as problematic by the IG include such household names as Lenovo computers, Lexmark printers, and GoPro cameras.
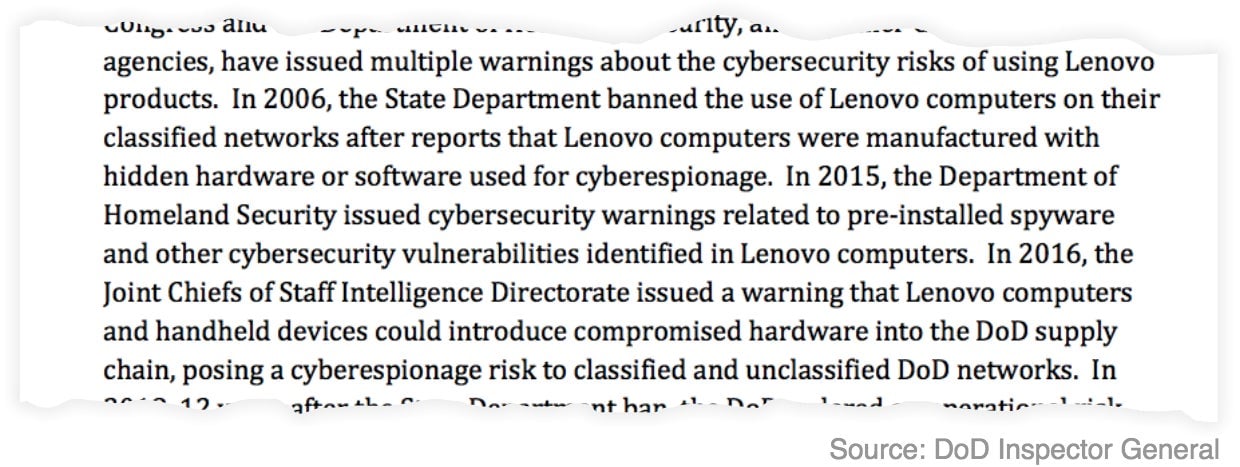
Lenovo
In 2006, the report notes, the State Department banned Lenovo products from its classified networks after reports that the company’s computers were being manufactured with hidden spyware and backdoors. In 2015, the DHS issued a warning about cybersecurity vulnerabilities in Lenovo devices, and in 2016 the Joint Chiefs of Staff Intelligence Directorate warned that Lenovo hardware posed a cyberespionage risk to both classified and unclassified networks and had the potential to compromise the entire DoD supply chain.
Still, the Army purchased 195 Lenovo products last year, for around $268,000, while the Air Force acquired 1,378 Lenovo products for $1.9 million.
Lexmark
Last year, the Army and Air Force bought more than 8,000 Lexmark printers for about $30 million. The company is owned by a consortium of Chinese firms, and has links to the country’s military, nuclear, and cyberespionage programs, points out the IG report. A US government vulnerabilities database lists 20 known cybersecurity concerns pertaining to Lexmark, such as “storing and transmitting sensitive network access credentials in plain text and allowing the execution of malicious code on the printer,” which the IG says “could allow remote attackers to use a connected Lexmark printer to conduct cyberespionage or launch a denial of service attack on a DoD network.”
GoPro
The Army and Air Force also purchased 117 GoPro cameras last year, costing $98,000. The built-in wireless and Bluetooth capabilities, which let users share video in real-time, “have vulnerabilities that could allow a remote attacker access to the stored network credentials and live video streams,” says the report. “By exploiting these vulnerabilities, a malicious actor could view the video stream, start recording, or take pictures without the user’s knowledge.”
The DoD’s response to the IG report is almost entirely redacted.
Next steps?
The DoD must start to identify, assess, and mitigate cybersecurity risks posed by off-the-shelf technology before it is put into use, cautions the IG. However, the report points out that current DoD policy only mitigates cybersecurity risks “after purchase.”
“Despite DoD policies and the numerous organizations performing cybersecurity testing and analysis,” says the audit, “there appears to be no organization assessing the risks for COTS items DoD-wide, identifying high-risk items for further testing, or actively recommending prohibition of these high-risk items when necessary.”
It’s a serious enough problem that the IG believes a legislative fix might be the only answer.
In the meantime, says the report, “We recommend that the Secretary of Defense direct an organization or group to develop a risk-based approach to prioritize COTS items for further evaluation, a process to test high-risk COTS items, and a process to prohibit the purchase and use of high-risk COTS items, when necessary, until mitigation strategies can limit the risk to an acceptable level.”