The essential tools and habits for reclaiming your data privacy
Fears over online privacy are intensifying worldwide. Three-quarters of global internet users surveyed by CIGI-Ipsos say they’re worried, and most of them say their fears have only grown in the last year. With Big Tech privacy scandals and crackdowns on reporters and ordinary citizens in countries like the US and China, it’s easy to see why.


Fears over online privacy are intensifying worldwide. Three-quarters of global internet users surveyed by CIGI-Ipsos say they’re worried, and most of them say their fears have only grown in the last year. With Big Tech privacy scandals and crackdowns on reporters and ordinary citizens in countries like the US and China, it’s easy to see why.
Many internet users know they want to protect their personal data, but how to do that isn’t always obvious. Quartz’s latest presentation introduces you to tools that can help keep your data secure.
Threat modeling is the first step in protecting yourself online. You need to identify the actor you’re trying to keep from accessing your data. This could be as general as an opportunistic hacker looking for poorly-guarded accounts or as specific as the corporation you are investigating or protesting against.
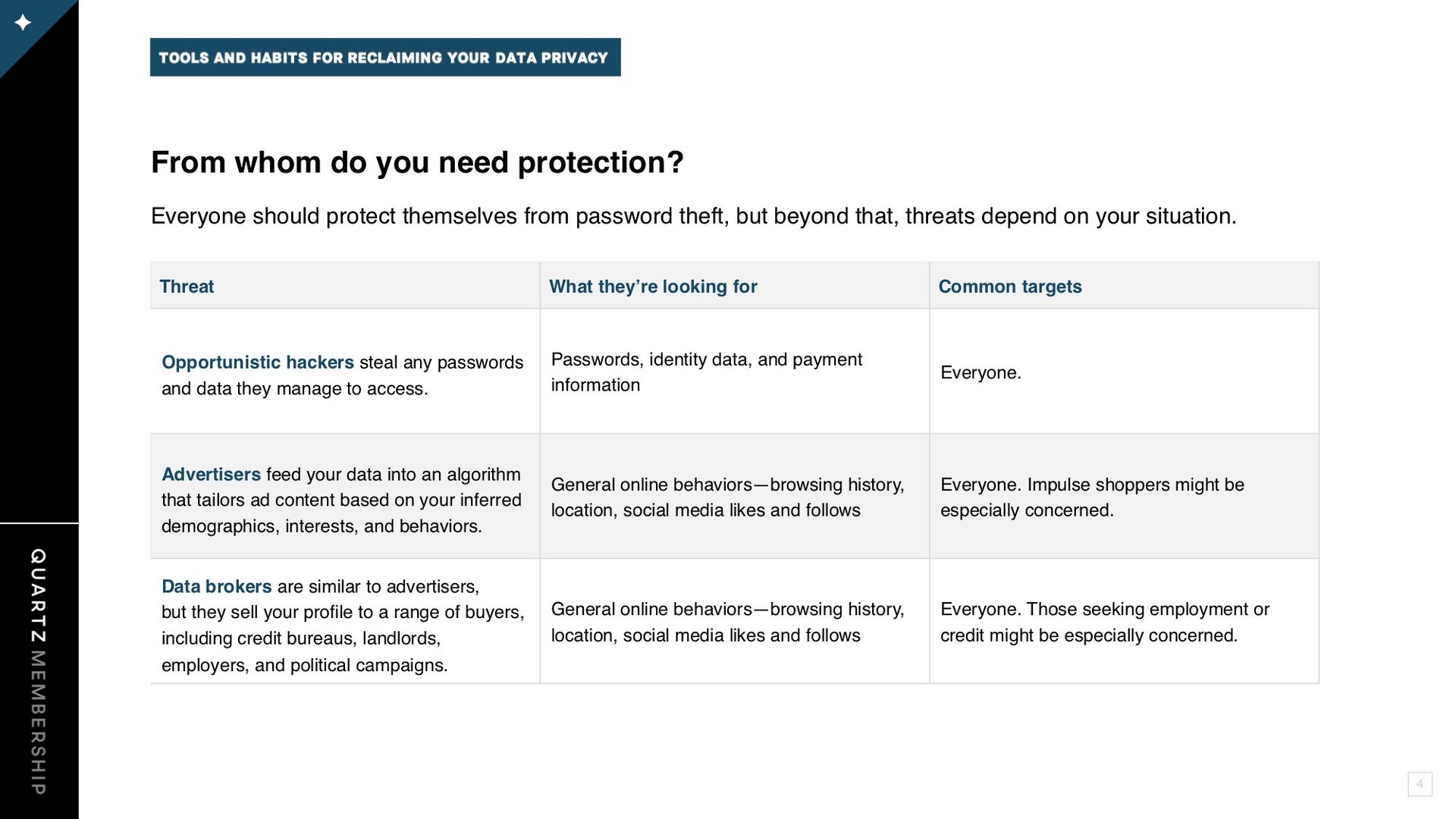
Each potential threat wants different data and requires specific protections. Once you understand your threat model, you can implement the tools that will offer the best defense. You can also form habits that bolster your general safety online.
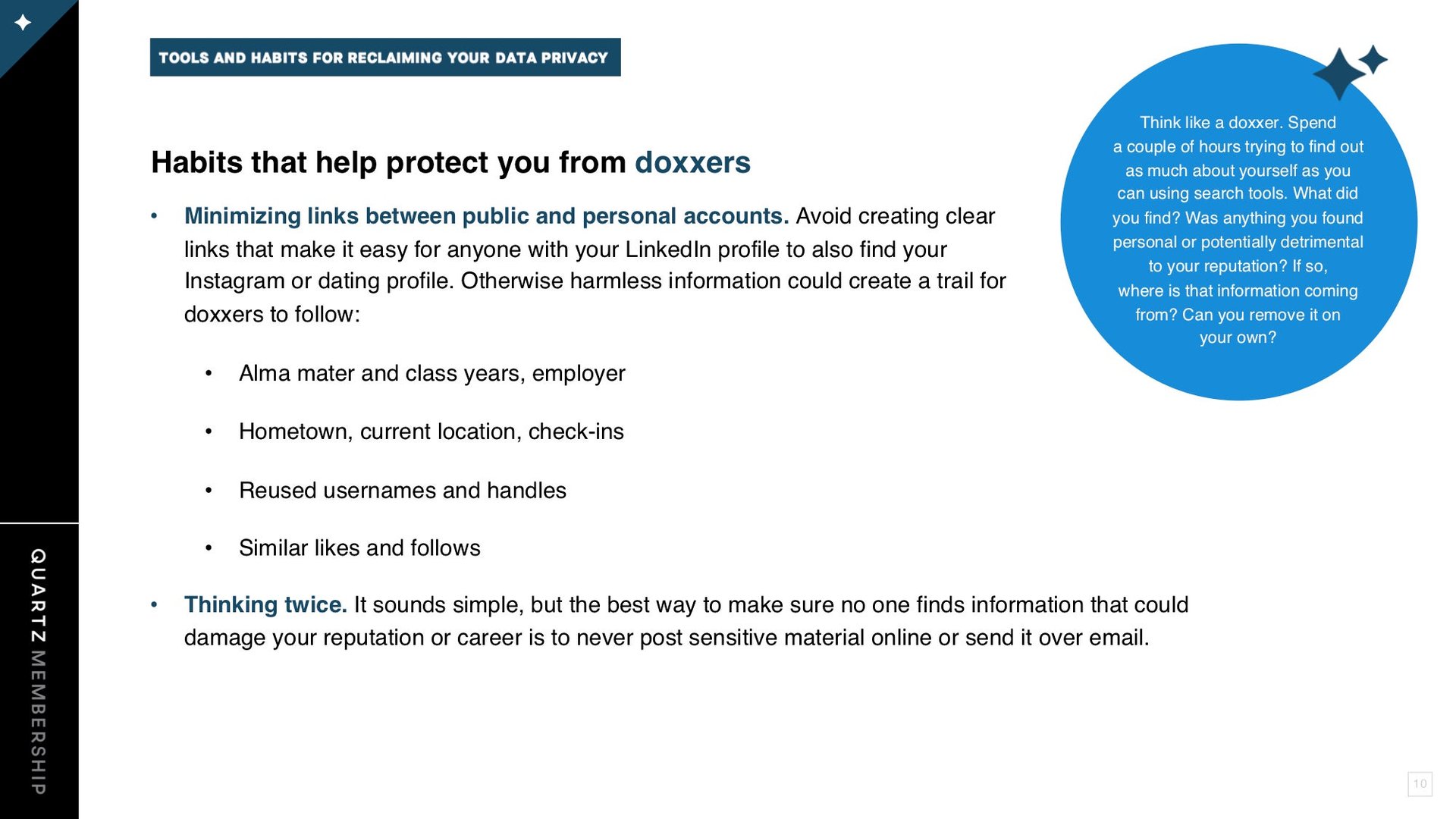
To see all of the slides, you can view the PDF version or download the PowerPoint file, which includes our sources and notes. This is one of an ongoing series of member-exclusive presentations, which you can read, reformat, and use as you wish.
Please share any feedback about what would make these presentations more useful—or topics you’d like to see us cover—by emailing us at [email protected]. These presentations are an exclusive benefit for Quartz members. We’d love it if you’d encourage any friends or colleagues who express interest to become a member so they can access them too.