The Russian military used email phishing to target US election-related services, according to a leaked NSA document
Russian military intelligence engaged in a spear-phishing attack against an unnamed company in the US, “evidently to obtain information on elections-related software and hardware,” according to a top-secret National Security Agency (NSA) report, which was published on Monday (June 5) by The Intercept. The report says Russian intelligence agency also conducted phishing attacks against several government agencies and attempted to impede requests for absentee voting ballots.

Russian military intelligence engaged in a spear-phishing attack against an unnamed company in the US, “evidently to obtain information on elections-related software and hardware,” according to a top-secret National Security Agency (NSA) report, which was published on Monday (June 5) by The Intercept. The report says Russian intelligence agency also conducted phishing attacks against several government agencies and attempted to impede requests for absentee voting ballots.
Shortly after The Intercept published the NSA document, the US Department of Justice announced that the FBI had arrested a 25-year-old contractor in Georgia, Reality Leigh Winner, and charged her “with removing classified material from a government facility and mailing it to a news outlet.” The DOJ’s announcement did not mention The Intercept, and officials have not confirmed a connection between the article and the arrest. However, several key details between the article and an affidavit released by the DOJ, such as the date of the document in question, match up.
The report as published by The Intercept details operations that took place in August and October of 2016, just before the US presidential election on November 8. It contradicts recent statements made by Russian president Vladimir Putin, who said last week that while “patriotic” Russian civilians may have engaged in hacking, the Russian government did not. He also suggested in an interview with NBC on Friday that hackers in the US may have framed Russia.
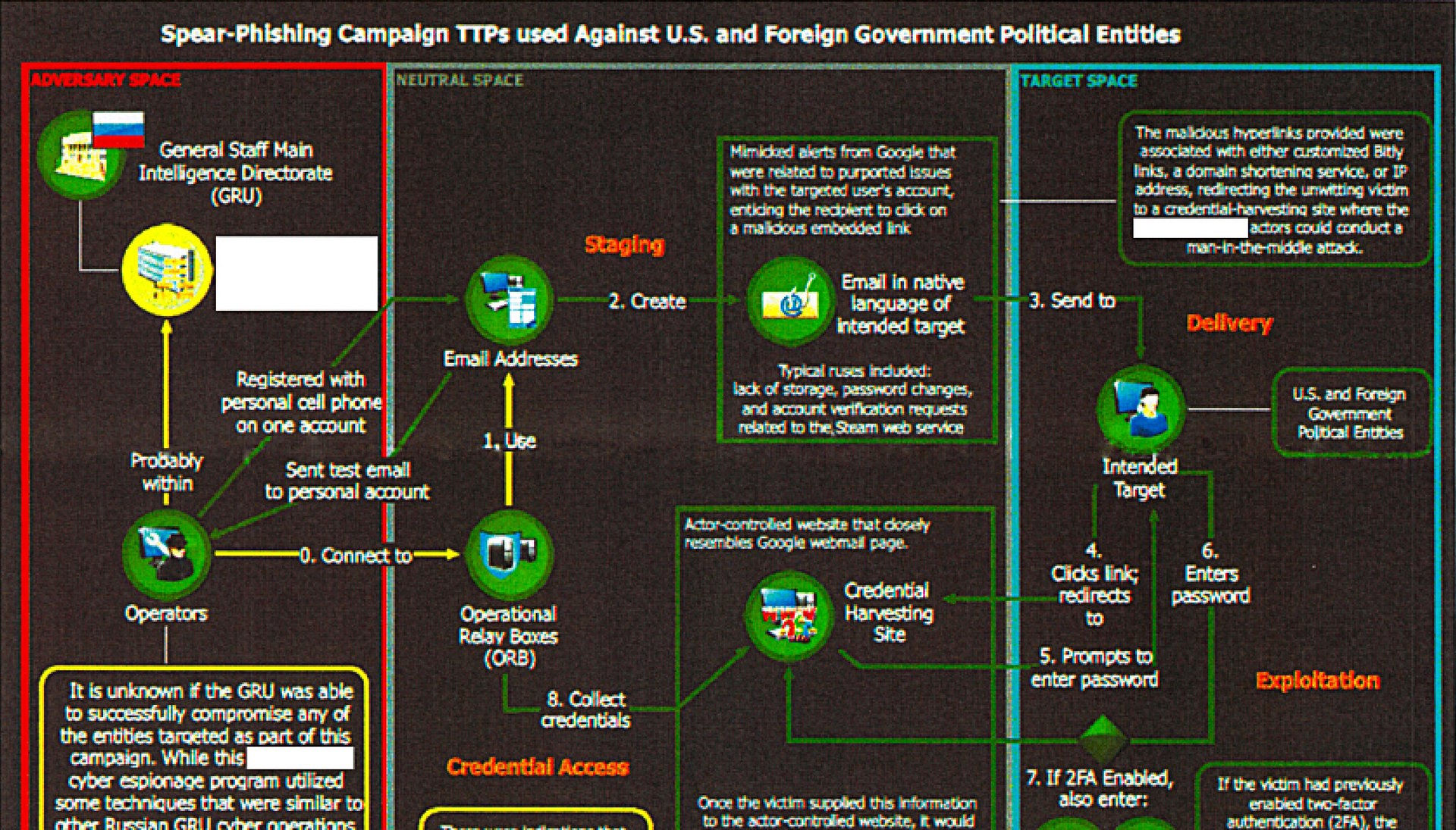
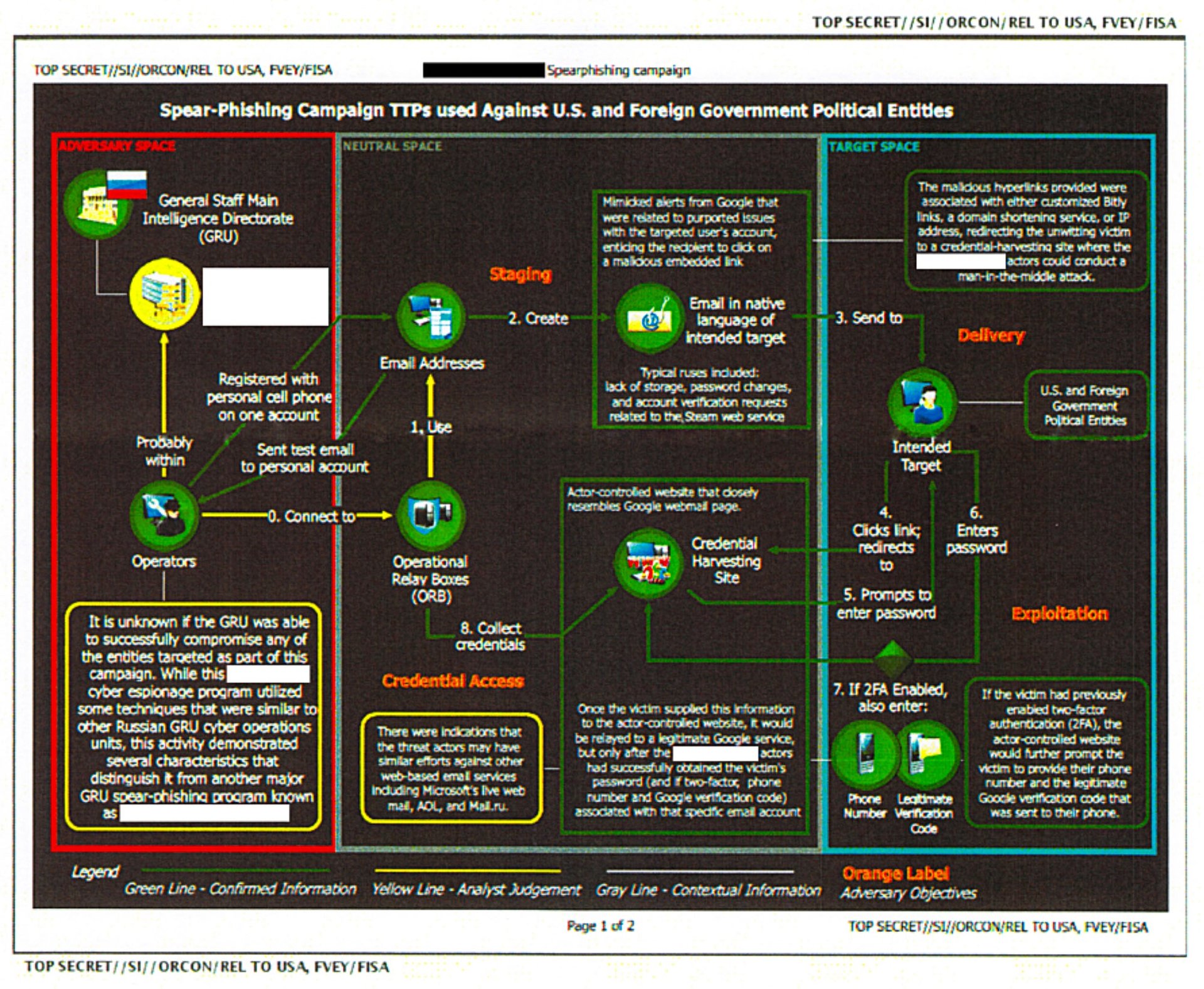
The NSA document explicitly says otherwise, calling out Russia’s General Staff Main Intelligence Directorate (GRU, for the agency’s name in Russian), the country’s military intelligence agency, as the main actor behind the operations.
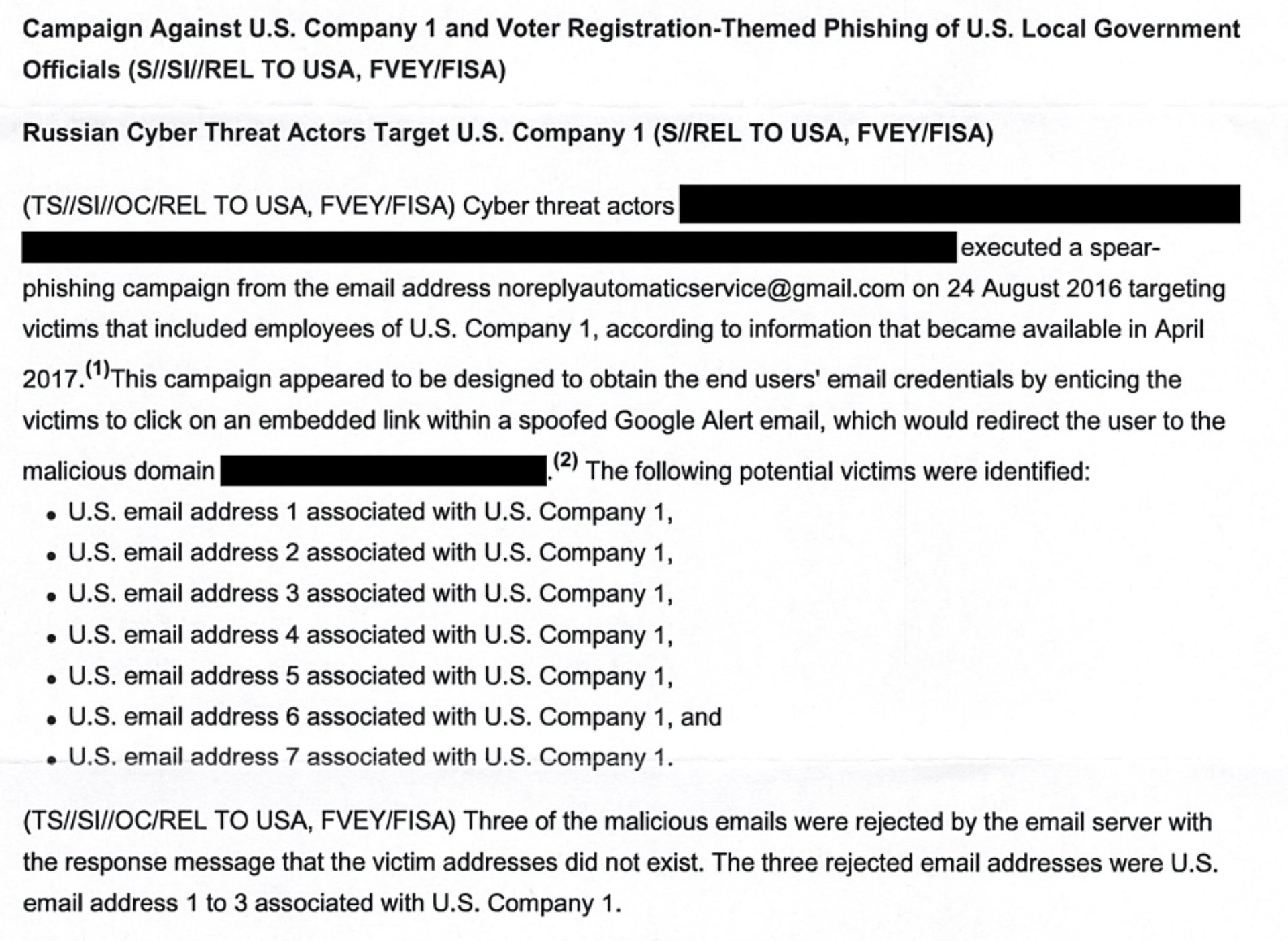
On August 24, the GRU “executed a spear-phishing campaign from the email address [email protected],” according to the report, sending fake Google Alert emails to employees of a US company apparently involved in developing election systems. When employees clicked a link in the email, it took them to what appeared to be a legitimate Google login page. If they entered their login credentials there, the hackers captured them.
A comment in the NSA report notes that at least one employee’s account was “likely” compromised.
With the information obtained in that attack, the GRU launched a second phishing campaign against “US local government organizations” in October, according to the report. The hackers created the email account “[email protected],” which used the name of the elections-services company as its display name. From that account, the hackers sent 122 phishing emails to local government agencies, offering “election-related products and services.”
Those emails contained two Microsoft Word documents as attachments, both of which were “trojanized with a Visual Basic script, which, when opened, would spawn a PowerShell instance and beacon out to malicious infrastructure,” the report states. That is, once an attached Word document was opened by the victim, the malware would execute commands through PowerShell that connected the computer to an IP address within the US. It then downloaded “an unknown payload,” which then installed another piece of software the NSA believes was used to “establish persistent access or survey the victim for items of interest.”
The hackers also appear to have attempted to create email addresses that would intercept requests for absentee ballots by “mimicking a legitimate absentee ballot-related service provider.” In the 2016 election, millions of Americans voted by sending in absentee ballots.