If the Chinese army is trying to hack a Missouri water plant, what else is it infiltrating?
The question of whether the Chinese military is on a hacking offensive has largely been answered—and, despite Chinese government protestations, it sure looks like a pretty big “yes.” However, beyond the widely reported infiltration of foreign companies, the question of what else it’s hacking remains hazy.


The question of whether the Chinese military is on a hacking offensive has largely been answered—and, despite Chinese government protestations, it sure looks like a pretty big “yes.” However, beyond the widely reported infiltration of foreign companies, the question of what else it’s hacking remains hazy.
But new research confirms one of the scarier possibilities: that the Chinese army is going after critical US infrastructure.
This all came out of a project by Kyle Wilhoit, a researcher at a security company called Trend Micro, that set up decoy “honeypots,” as decoy infrastructure systems are known, in 12 different countries. Wilhoit’s construction of a rural Missouri water plant honeypot attracted the notorious APT1, a crackerjack Chinese military hacking team sometimes known as Comment Crew, according to research he presented at the Black Hat security conference in Las Vegas. The group gained access in December 2012 through a Microsoft Word document containing malware unique to APT1.
“I actually watched the attacker interface with the machine,” he told the MIT Technology Review, referring to APT1. “It was 100% clear they knew what they were doing.”
Wilhoit noted to CBSNews.com that systems like power grids and water plants are inherently vulnerable to hacking threats because they’re using outdated technology and don’t necessarily prioritize security. Of the “critical” honeypot attacks—meaning those that could have taken control of the system—half came from China. Examples include turning the pump’s water temperature to 130˚ Fahrenheit and shutting down the system.
This suggests that Chinese hackers are taking control of critical infrastructure. ”These attacks are happening and the engineers likely don’t know,” Wilhoit told MIT Technology Review. Here’s a look at APT1’s past activity:
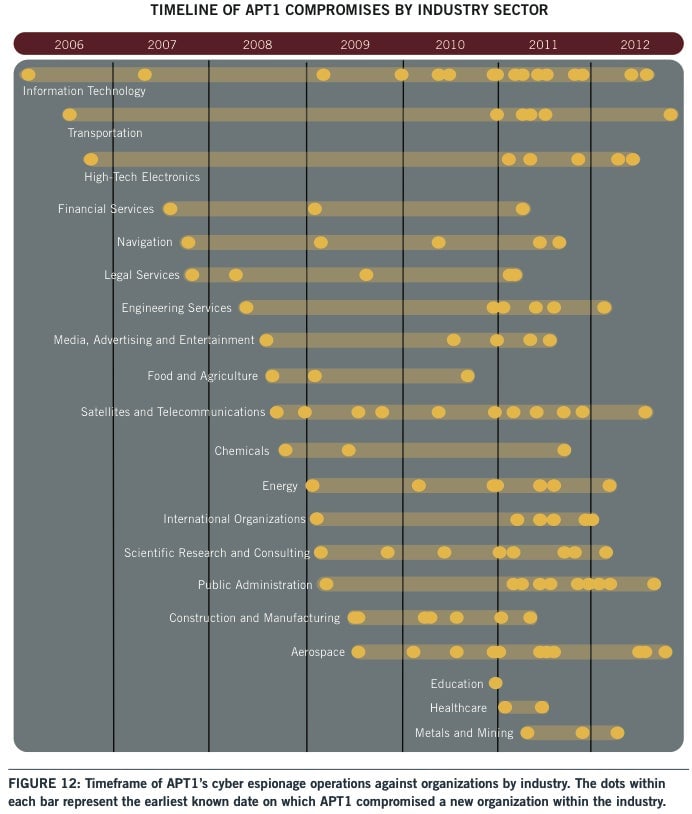
To date, the only publicly disclosed cyberattacks on US control systems have been on a factory and a state government building, both in New Jersey, reports MIT Technology Review. It’s unclear where those attacks originated.