US president Donald Trump describes Rudy Giuliani as a “great crime fighter,” yet almost three years after multiple shortcomings with Giuliani’s corporate website were first pointed out, the president’s personal lawyer has not brought it up to even the most rudimentary security standards.
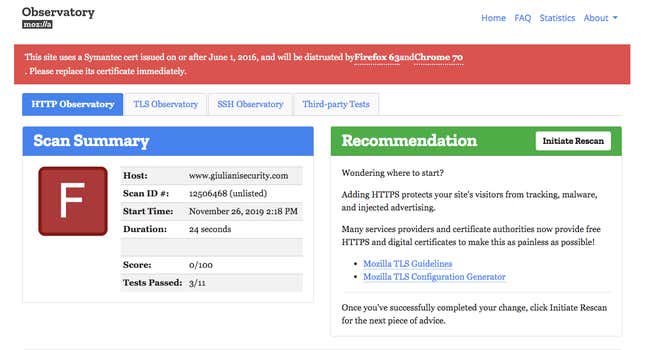
Mozilla Observatory, an online site-scanning service operated by the nonprofit company behind the Firefox web browser, rates Giuliani Security & Safety’s website an “F” for basic connection security, with a score of 0 out of 100. In a suite of 11 tests, the Giuliani Security & Safety site passes just 3, according to Mozilla.
“I’d love to become the person that comes up with a solution to cybersecurity,” Giuliani told Fox News shortly after the 2016 presidential election, referring to a possible position in the Trump White House. Trump appointed Giuliani as his cybersecurity adviser in January 2017.
However, the former New York City mayor can’t seem to adequately secure his own website from potential eavesdroppers.
Giuliani’s online foibles have been well-documented, and he is said to know little about cybersecurity. He has, among other things, locked himself out of his iPhone after forgetting the password and failing to get it right more than 10 times. Giuliani recently accidentally “butt-dialed” an NBC News reporter, inadvertently leaving a three-minute voicemail in which he discussed overseas deals and a need to raise a “few hundred thousand” dollars. At the same time, Giuliani boosters have described him as “perfectly suited” to oversee the president’s cybersecurity task force, focusing on his skills as a “facilitator.”
Web visitors to Giuliani Security & Safety are greeted with a warning that the site is “not secure.” This means the site, which features a testimonial from Gennadiy Kernes, the mayor of Kharkiv, Ukraine, who has been accused of having ties to organized crime, isn’t using a private connection, and the information a user sends or receives could be intercepted or altered. Giuliani Security’s SSL certificate has expired—an issue first raised in 2017—meaning the site’s identity can’t be trusted.

Ron Gula, who worked as a network penetration tester for the National Security Agency, told Quartz he has met Giuliani and came away impressed. He noted that the site, as presently configured, is little more than a “billboard” for Giuliani’s business, and since it doesn’t ask for passwords or other sensitive data, it doesn’t require strong defenses.
The site is “pretty basic,” and isn’t asking users to transmit sensitive information through it, agreed Josh Mitchell, a cybersecurity consultant at Nuix, an Australian technology firm. At the same time, if it is indeed an advertisement for Mr. Giuliani’s services, Miller questions his team’s cybersecurity acumen if “they can’t install a website properly.”
“We’re happy to see that Mr. Giuliani attempted to encrypt traffic to his company’s site,” said Max Hunter, engineering director at the nonprofit Electronic Frontier Foundation, in an email. “Manually configuring a certificate is a frustrating, time-consuming process with opportunities for embarrassing misconfigurations like this one,” Hunter said. The EFF has worked to make securing websites easier, and Hunter recommended that Giuliani check out its free “certbot” tool to do just that.
Giuliani did not respond to a request for comment.
