Their tools had fearsome names–social engineering, SQL injection, spear phishing. Their marks had plenty to lose–oil and gas financial records and proprietary technology. For a while, the hackers won.
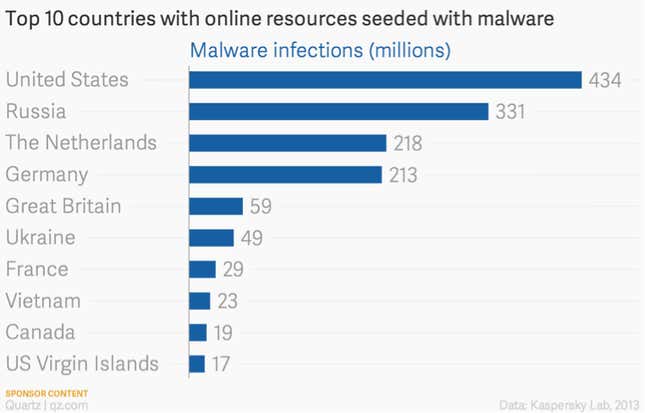
To strengthen the security community, a 2011 McAfee report called “Global Energy Attacks: ‘Night Dragon’” disclosed these breaches, which began in 2009. The report traced a group of hackers to China, which was a leading source of malware at the time (it has since dropped out of Kaspersky’s top ten due to improved enforcement).
The hackers’ methods were straightforward but coordinated attacks that used public website intrusions (SQL injection) or emails with nefarious links (spear phishing) to plant remote administration tools (RATs) on internal networks. The RATs ran rampant there, feeding on a company cloud.
“These people seemed to be more like company worker bees rather than free-spirited computer hackers,” McAfee’s vice president for threat research told the New York Times. “These attacks were bold, even brazen, and they left behind a trail of evidence.”
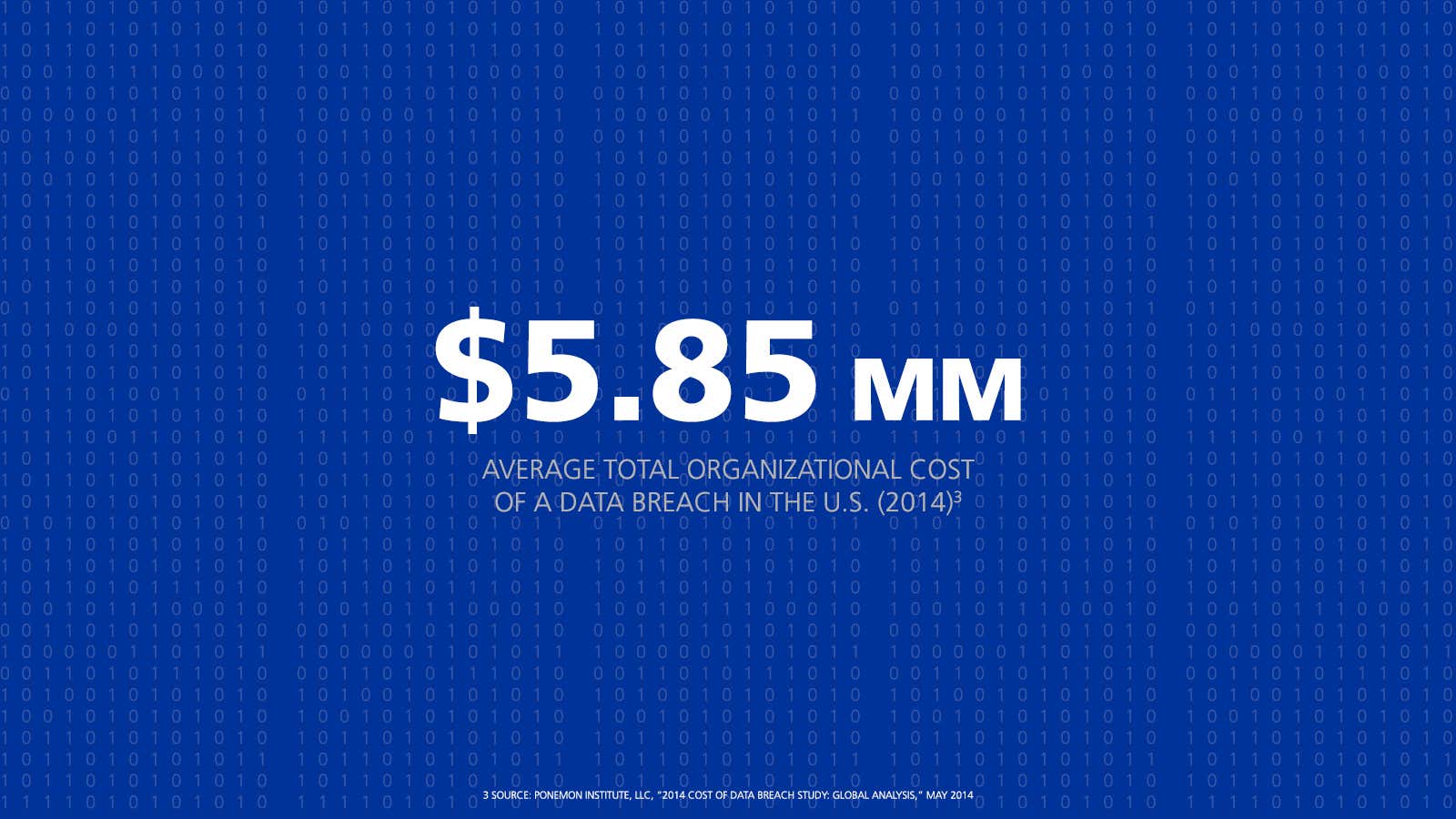
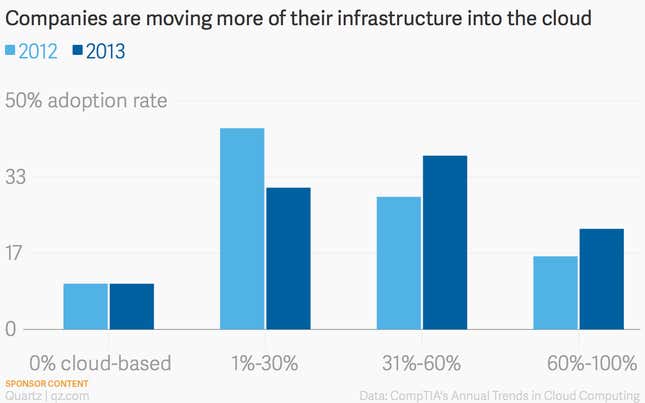
As our devices and data become more connected than ever, so do the hackers targeting them. Prototypical exploits like Night Dragon and those of the infamous TJX hacker are linked to global technology and expertise rather than the archetypal solo, hero hacker. And methods continue to evolve. Companies moving to the cloud for flexibility and scale, particularly those with troves of intellectual property, can attract hackers betting on a lag in cloud security. The cloud is an attractive target because of what’s found lurking within. Data, whether it’s personal information, intellectual property, or trade secrets, is the currency of today’s cyber criminals.
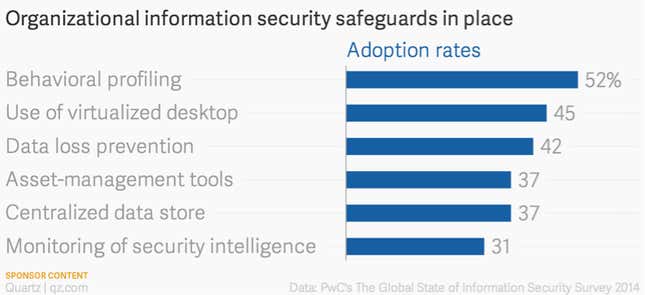
Rushing to the cloud for its power while discounting its unique architectural demands can breed disaster. The flatness and openness that give the cloud its strength can also make it vulnerable. If the foundational or host hardware and operating system are compromised, every workload hosted there can be exploited as well. This is hyperjacking, and it’s just one of the ways hackers are cutting through clouds.
Due to the complexities of the cloud, even the most resilient organizations can be left vulnerable from their reliance on cloud computing. “Physical perils such as lightning and other storm activity have caused more downtime than cyber-attacks to date,” Jim Charron, Technology Practice Leader at Zurich North America, recently said. “Weather events, like cyber events, are unpredictable, increasingly severe, and can strike anywhere.” Yet growth continues, and it looks like IT will have cloud cover for some time.
What the rise of the cloud will mean outside of IT meetings is an even more open question. As more individuals send more personal data to servers via apps and websites, they are enmeshed in algorithms spinning to analyze and capitalize on each byte.
Just like eager companies, people seduced by new technology can fail to consider who is actually accessing their data and how it’s being used–let alone how much they should trust nascent systems in the first place.
Data is a precious asset and a juicy target. As it floats skyward, its protectors must stay grounded.
For more information on the risks of cloud computing, click here.
If you would like to receive alerts when new BULLETIN installments are published, sign up here.
This article was produced on behalf of Zurich by the Quartz marketing team and not by the Quartz editorial staff. Zurich neither endorses nor rejects the recommendations of the discussion presented. Further, the comments contained in this newsletter are for general distribution and cannot apply to any single set of specific circumstances. If you have a legal issue to which you believe this article relates, we urge you to consult your own legal counsel. Quartz is not a subsidiary or affiliate of Zurich.