The US FBI told the Democratic National Committee in September of 2015 that its computer network had been breached by hackers linked to the Russian government. But nothing concrete happened about the cyber break-in for seven months, according to an exhaustive report on Dec. 13 in the New York Times (paywall).
Instead, DNC workers committed a sequence of jaw-dropping blunders. Combined with tech practices that ignored even the most basic rules of cyber safety, this allowed hackers to rummage through the DNC’s server, downloading tens of thousands of private emails which were ultimately published on Wikileaks. (The FBI agent tasked with warning the DNC was also strangely lackadaisical about it, doing little more than leaving a series of voicemails after speaking to an IT temp, though the DNC’s headquarters are just a half mile from the FBI’s own.)
It is impossible to tell whether the hack, and a related one that breached the email account of Hillary Clinton campaign chairman John Podesta, played a significant part in Clinton’s election defeat. But the situation certainly hobbled Democrats, sidelining some “at the height of the campaign,” as the Times notes, while also potentially affecting “congressional races in a dozen states.”
Russian hackers are suspected of having targeted everyone from NGOs to consumer tech companies like LinkedIn and Dropbox in recent months. But even if you or your company think you aren’t important enough to be in their sights, many of the techniques they use are common to hackers everywhere. Here’s how to protect against them.
How to not get phished
The hackers first gained access to the DNC computer network using the commonest weapon in a hacker’s arsenal: a phishing attack.
A Clinton campaign official received an email that looked like it was from Google with the subject line “Someone has your password.” It claimed someone had tried to log into his account from an IP address in Ukraine. The official clicked on a link in the email that said CHANGE PASSWORD, and did so. In fact, the link led to a server controlled by the hackers, letting the Russians into his email.
Many other DNC and Clinton campaign staff were similarly targeted. Podesta fell victim when a staffer sent an email warning that the phishing email was illegitimate, but accidentally typed “legitimate” instead, causing Podesta to click on the password link. The mistake, the aide told the Times, had “plagued him ever since.”
Google tends towards less dramatic language than “Someone has your password,” such as ”New sign-in from iPhone” or “Review blocked sign-in attempt.” The links or buttons in its emails will usually tell you to review information, rather than shouting CHANGE PASSWORD.
Here’s what one of the fake emails looked like:
Here’s a real Google notification:
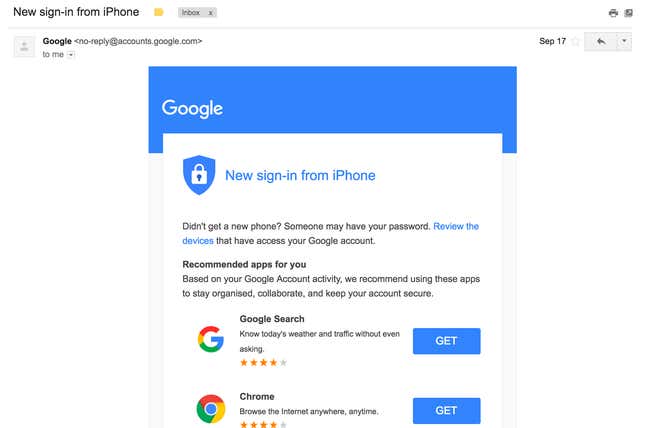
There are many potential clues that an email may be a phishing email, but the simplest and safest way to spot one is to check any link in it before you click—hover your mouse over it, or on a phone, press and hold your finger on it—and make sure it’s actually to a URL from the company that supposedly sent it.
And when you look, look closely. Often hackers will substitute one or two characters so a URL looks similar—goog1e.com or app1e.com, for instance. Sometimes, an email will display one URL but the underlying link will be different, like in this case: apple.com.
If you run a big company
Make sure your IT department is empowered, and capable of monitoring hacks. The DNC was relying on a part-time contractor for much of its tech support. When the FBI first called to tell him it suspected there was malware on the DNC systems, he thought it might be a prank. Left mostly on his own to figure out how to respond, he checked the DNC’s systems for the malware, but couldn’t find it. The DNC also lacked tools that let tech staff watch for suspicious activity on the network, a telltale sign that hackers have paid a visit.
Any company with more than a few employees that uses the internet should have people on staff with experience and resources for dealing with cyber threats. These staff also tend to be pretty good at the more basic IT tasks like making your printers work.
When the FBI calls, call back. The DNC’s part-time contractor didn’t return subsequent follow-up calls from the FBI agent, because he wasn’t sure he was real. But the FBI has a main switchboard you can call. It can’t be that hard to check.
If you run any size company, or work alone
Use two-factor authentication. Even if you fall for a phishing scam, there’s a safeguard. Many of the most popular apps on the web, from Gmail to Slack to Facebook, have an optional second layer of security. When you log in from a new device (or often a new place), they ask you to enter an extra code, which is sent by text message or generated by an app on your phone. That way, even if hackers have your password, they can’t get in unless they’ve also stolen your phone. Here’s how to turn on two-factor authentication.
Use a password manager. You probably use dozens of websites and services that require a password. Most people use the same password on many (or all) of them. This is a terrible idea. Apps like 1Password or LastPass create and store long, complicated passwords for each service you use that are far harder to crack than any password you’re likely come up with. You then have to remember just one (also long, but you can make it easy to remember) password to log into the app. This also allows teams to securely share logins between teammates.
Use more secure messaging systems than email. If you’re very paranoid, SpiderOak, recommended by clandestine whistleblower Edward Snowden, has multiple encrypted tools to help businesses or political candidates run their operations. SpiderOak’s synonymous tool is a cloud-based document-sharing service, similar to Dropbox. It also produces Semaphor, an encrypted group chat service similar to Slack. For text-message-style communication, many apps offer end-to-end encryption, which conceals the contents of your messages from snoopers; but the app preferred by the ultra-cautious is Signal, produced by Open Whisper Systems.
Have important conversations in person or over the phone. One of the most telling revelations from the DNC emails was just how much behind-the-back sniping was going on, embarrassing staffers and causing rifts between party members. If nasty things really need to be said about your colleagues or your boss, don’t say them in communications channels that come with permanent records. Say them over coffee in the break room, or a beer after work. And if you can’t, many chat apps, such as WhatsApp and Signal, also let you hold secure, fully encrypted voice or video calls.
Correction: An earlier version of this story said that the Signal app was produced by SpiderOak, not by Open Whisper Systems.
