Even after a partial military disengagement in February 2021, China’s surveillance of India may not have ended.
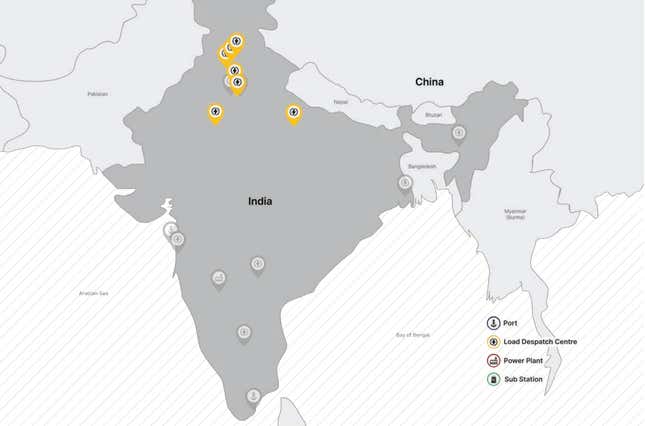
In recent months, Chinese state-sponsored hackers, dubbed Threat Activity Group 38 (TAG-38), have targeted at least seven state load dispatch centres (SLDCs) that carry out real-time operations for grid control and electricity dispatch in India, according to Recorded Future, a US-based threat intelligence firm.
They also allegedly targeted a national emergency response system and the Indian subsidiary of a multinational logistics company.
The cyberattacks have been “geographically concentrated” along the disputed India-China border in Ladakh, Recorded Future’s research shows. India’s power minister RK Singh has also brought up this issue.
China has hacked India before
Between mid-2020 and February 2021, Recorded Future had reported a similar intrusion into India’s power grid by a group called RedEcho which is known to have China links. At that time, 10 distinct Indian power firms, two ports, a large generation operator, and other operational assets, were compromised.
The prolonged targeting “offers limited economic espionage or traditional intelligence-gathering opportunities,” according to Recorded Future. Instead, it is “likely intended to enable information-gathering surrounding critical infrastructure systems or is pre-positioning for future activity.”
How China spies on India
People’s Liberation Army (PLA) and groups linked to the Chinese ministry of state security (MSS) have been using ShadowPad, a privately shared modular backdoor software, to compromise and co-opt internet-facing digital video recorders or internet protocol cameras—the ones used in closed-circuit television (CCTV) networks. The devices used to launch the infiltrations were traced to Taiwan or South Korea.
How can India beef up cybersecurity?
China “firmly opposes and combats any form of cyberattacks, and will not encourage, support, or condone any cyberattacks,” the country’s foreign ministry spokesman Zhao Lijian told reporters yesterday (April 7).
India, however, needs to up its guard anyway. It must monitor for consistent anomalous outbound traffic from its network to unusual servers, Recorded Future recommends.
The authorities should ensure that software and firmware associated with internet-of-things devices, like camera systems, are up to date. Moreover, good tech hygiene, like keeping complex passwords and turning on two-factor authentication (2FA), is a must.
Lastly, Recorded Future suggests going back to the basics: “Where possible, avoid exposing these devices directly to the internet.”
