After making just $10,000 from a global ransomware attack last week, the hackers behind the scheme are trying to make up for the paltry returns by selling a master decryption key that will unlock any computer that was infected. For a quarter of a million US dollars apiece.
“Send me 100 Bitcoins,” the hackers wrote in a message posted online on July 4, “and you will get my private key to decrypt any harddisk (except boot disks).”
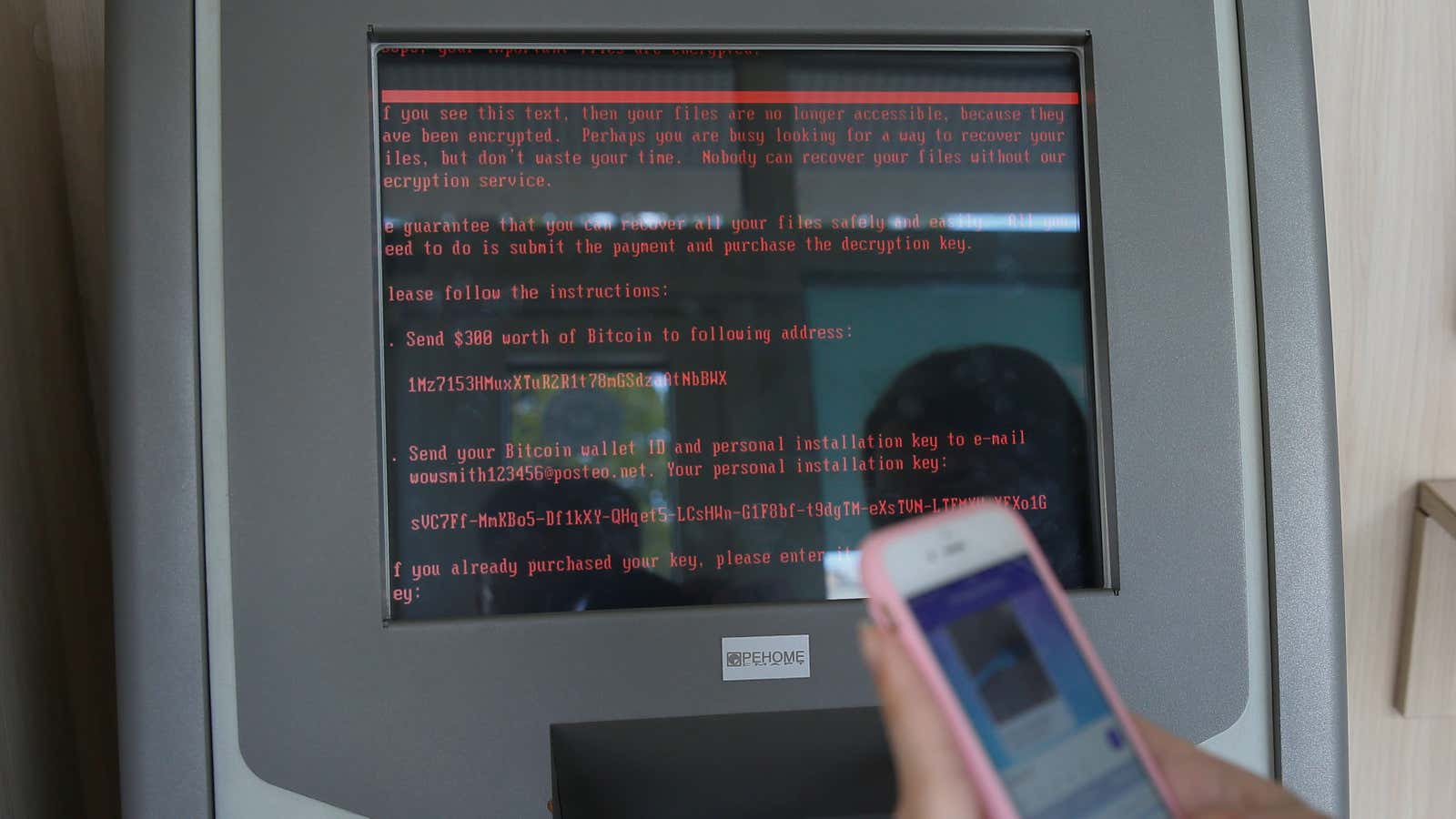
The Petya/NotPetya computer attack shut down critical services in Ukraine last week, then spread throughout Europe and the United States, locking users out of their files and demanding they pay $300 in bitcoin to get them back. A message appeared in red text over a black background on the infected computers, providing a bitcoin address where ransom payments should be sent. Once they paid, the message said, the victims were to send an email to [email protected]. The hackers would then verify their payment and send them a decryption key to unlock their files.
But a few hours after the virus started spreading, the Berlin-based email provider Posteo learned that the hackers were using its service and shut down their account. It meant that infected users had no way of contacting the hackers to regain access to their files, and in turn victims had no incentive to pay the ransom. The payments stopped in less than 24 hours, and the hackers had received only $10,000.
A week later, on July 4, money began moving out of the bitcoin account the hackers used to receive ransom payments. The transactions were first reported by a bot Quartz setup, @petya_payments, which sends tweets any time it sees activity on the Petya/NotPetya account. In the first transaction, at 5:32 p.m. ET, the hackers sent about $340 to a bitcoin address owned by DeepPost, a service on the dark web that allows users to anonymously post public messages.
Two minutes later, they sent $316 to an address owned by PasteBin, which also allows users to post messages anonymously and is accessible on the normal internet.
Shortly before those transactions occurred, the hackers had posted the aforementioned message on both of those sites, offering to sell a master decryption key for 100 bitcoins, or roughly $260,000 USD. The hackers presumably sent the payments to prove the messages were genuine.
About 35 minutes later, the remaining bitcoins were moved to another account, and have stayed there since:
Security researchers have continuously speculated that the Petya/NotPeta attack was politically motivated and not about the money. The Ukrainian government has accused Russia of masterminding the attack. Russia has denied any involvement.
That funds have now been moved out of the original account may suggest something about the identity of the hackers, but it’s not yet clear what that is. It could just as easily be a government attempting to throw off investigators as an independent hacker or group trying to make a quick buck. And although the virus hit large companies around the world—including the British advertising agency WPP, the Danish shipping and oil group Maersk, and the pharmaceutical giant Merck in the United States—it’s likely far too late to expect any of those companies, or anyone, to pay $260,000 for the master key.