Mobile dating app Tinder appears to have exposed the physical location of its users for much longer than a “few hours,” as the company’s chief executive claimed. New evidence suggests the privacy breach dated back at least two weeks.
Quartz reported yesterday that the data files sent from Tinder’s servers to its apps had been revealing sensitive information about users, including their last known location and Facebook ID. Reaction to the piece centered on the fact that Tinder hasn’t disclosed the issue to its users. CEO Sean Rad said one reason they haven’t is that the breach didn’t last very long: ”An engineer basically found a hole that was there for like an hour,” he said in an interview yesterday.
But that wasn’t the first time the issue reared its head. Interviews with several people who have worked with Tinder’s API, which is how the company’s servers communicate with its apps, extend the timeline of the privacy breach considerably. Exactly when the issue began and at what points it remained a problem are still unclear. The company won’t provide details on the timing.
Rad hasn’t returned emails and phone calls seeking comment today. Justine Sacco, a spokeswoman for IAC, which owns Tinder, acknowledged the earlier breach but said it was fixed quickly, which isn’t supported by Quartz’s reporting. In a statement today, Sacco said:
On two different occasions, we became aware that our API was returning information that it should not have been. In both occasions, we promptly addressed and fixed the glitch. With respect to location data, we do not store the current location of a Tinder user but rather a vague/inaccurate point in space. We are extremely committed to upholding the highest standards of privacy and will continue to take all necessary steps to ensure our users’ data is protected from internal and external sources.
Tinder informed on July 8
Mike Soares, an engineer in San Francisco, says he discovered the issue on July 8 and immediately informed the company in an email to help@gotinder.com. The subject line was, “Privacy Hole With Your App,” and it detailed how Tinder’s API was returning more information than necessary, including the location and Facebook data.
Tinder needs to record each user’s last known location in order to suggest other people within a certain distance. But no one is supposed to see a user’s exact location, a privacy violation that could be considered especially egregious because Tinder is used to find people to hook up with. An introductory screen when first signing up for Tinder assures, “Your location will never be shown to other users.”
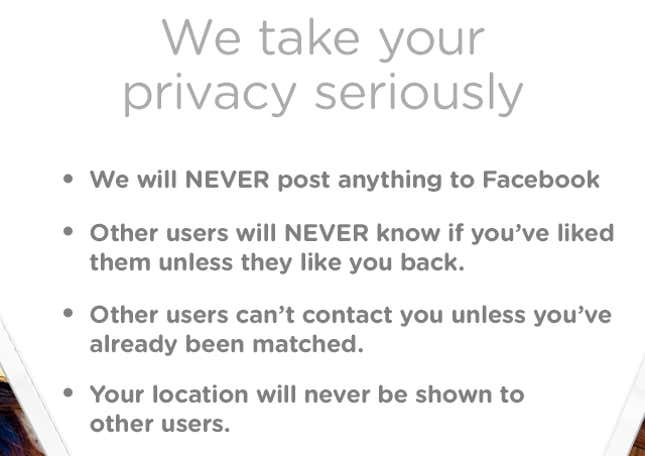
What Tinder’s API exposed
In his email to Tinder, Soares included data that he was able to access. Here is a small snippet of the data, focusing on fields that revealed sensitive information (with the specific data changed so as not to commit our own privacy violation):
"birth_date": "1992-06-24T00:00:00.000Z","gender": 1,"name": "Daisie","pos": {"lon": -73.9977375759311,"lat": 40.72255556095288 },"fbId": "185"
The “lon” and “lat” fields, for longitude and latitude, reveal the most recent location where “Daisie” was using Tinder. The “fbId” field reveals her unique ID number on Facebook (it’s actually mine), which could easily be used to find her last name.
The location data recorded by Tinder are only updated when someone uses the app, so it could be out of date. And to save battery life, Tinder uses a less precise reading of the user’s location than it could. Rad, the CEO, said in an interview yesterday, “We were not exposing any information that can harm any of our users or put our users in jeopardy.”
No reply from Tinder
Soares says he didn’t hear back from Tinder after his July 8 email. On July 14, he tried contacting the company again, this time over Twitter, and received a response. The next day, July 15, a Tinder employee emailed him: “I chatted with our CTO today and we’re currently sending down extra info that isn’t even needed currently. We’re going to patch this today to fix the problem.”
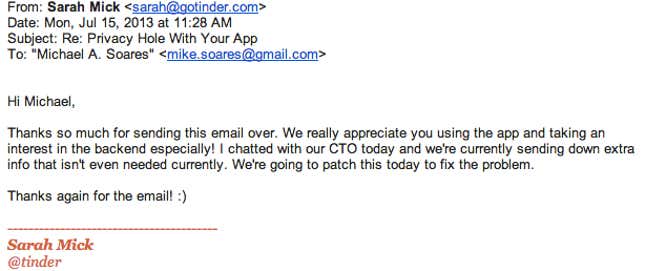
Tinder says it did fix the issue on July 15, but it cropped up again in a code release related to its new app for Android phones. It’s not clear exactly when the issue reemerged and when it was resolved.
Another web developer, Chintan Parikh, separately took an interest in Tinder’s API and was able to access location and Facebook data from it as recently as this past Sunday, July 21. The issue was finally resolved, it appears, on July 21 or 22. Tinder says it acted within “hours” of the code release that re-introduced the issue. The company’s API no longer returns precise location information about users nor their Facebook ID numbers.
Potentially sensitive data remain
Tinder’s API, however, still includes some user data that could be considered sensitive, specifically users’ birthdates and the ID of the Facebook photographs used in their Tinder profiles. In theory, that could be sufficient to find the user on Facebook, identify her by first and last name, and potentially glean other information from elsewhere on the internet.
Tinder uses Facebook to make recommendations from among a user’s friends, friends of friends, and so on. It also draws on Facebook for photographs, biographical information, age, and first name, which are all displayed to other people within the app. But it’s not clear why Tinder’s API needs to include each user’s birthdate or any identifiable information.
Users probably have different expectations of privacy on Tinder. After all, the app is intended to facilitate dates and hook-ups between real people. Some users, though, would surely want to avoid being identified by most people on the service, revealing only their first name, age, and photo.
Tinder is based in Los Angeles and primarily owned by IAC, based in New York. IAC also owns Match.com, OkCupid, and other online dating services.
